I found a very interesting virtual machine on VulnHub that focuses on VoIP vulnerabilities. Since I haven’t seen any other VoIP resources, I thought it would be great to give this a try.
VulnVoIP is based on a relatively old AsteriskNOW distribution and has a number of weaknesses. The aim is to locate VoIP users, crack their passwords and gain access to the Support account voicemail.
The IP of the target machine is 192.168.80.131. Here are the results of the port scan:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 | |
Let’s look at that DNS server first:
dnsmasq is a lightweight DNS, TFTP and DHCP server. It is intended to provide coupled DNS and DHCP service to a LAN.
Dnsmasq accepts DNS queries and either answers them from a small, local, cache or forwards them to a real, recursive, DNS server. It loads the contents of /etc/hosts so that local hostnames which do not appear in the global DNS can be resolved and also answers DNS queries for DHCP configured hosts.
The dnsmasq DHCP server supports static address assignments and multiple networks. It automatically sends a sensible default set of DHCP options, and can be configured to send any desired set of DHCP options, including vendor-encapsulated options. It includes a secure, read-only, TFTP server to allow net/PXE boot of DHCP hosts and also supports BOOTP.
Dnsmasq supports IPv6 for DNS, but not DHCP.
There is a Heap Overflow and Null-pointer Dereference vulnerability affecting the TFTP server component:
CVE-2009-2957
A vulnerability has been found that may allow an attacker to execute arbitrary code on servers or home routers running dnsmasq with the TFTP service enabled (‘—enable-tfp’). This service is not enabled by default on most distributions; in particular it is not enabled by default on OpenWRT or DD-WRT. Chances of successful exploitation increase when a long directory prefix is used for TFTP. Code will be executed with the privileges of the user running dnsmasq, which is normally a non-privileged one.
Additionally there is a potential DoS attack to the TFTP service by exploiting a null-pointer dereference vulnerability.
I wasn’t able to exploit this though, so moving on.
Navigating to the web page, we see two links, for Voicemail & Recordings (ARI) and FreePBX Administration. The administration page requires HTTP authentication, and the other one is a login portal.
A Nessus scan revealed that the Asterisk Recording Interface uses a default set of credentials for the administrator’s account: admin/ari_password, on the URL http://192.168.80.131/recordings/index.php . I didn’t find anything useful even after logging in. These credentials didn’t work on the admin page at http://192.168.80.131/admin/config.php , but I was able to glean the FreePBX version from the webpage (2.7.0.0). Might come in handy later!
Since this is my first time doing anything remotely related to VoIP, I had some googling and reading to do. For a while I just digressed from the main goal of hacking this machine to burying myself in the Session Initiation Protocol RFC (ouch!), and 2 books: Hacking Exposed VoIP: Voice Over IP Security Secrets & Solutions and Hacking VoIP: Protocols, Attacks, and Countermeasures.
So, a short introduction to SIP is in order:
SIP is an application-layer control protocol that can establish, modify, and terminate multimedia sessions (conferences) such as Internet telephony calls. SIP can also invite participants to already existing sessions, such as multicast conferences.
SIP employs design elements similar to the HTTP request/response transaction model. Each transaction consists of a client request that invokes a particular method or function on the server and at least one response. SIP reuses most of the header fields, encoding rules and status codes of HTTP, providing a readable text-based format.
Each resource of a SIP network, such as a user agent or a voicemail box, is identified by a URI, based on the general standard syntax also used in Web services and e-mail. The URI scheme used for SIP is sip: and a typical SIP URI is of the form: sip:username:password@host:port
SIP clients typically use TCP or UDP on port numbers 5060 and/or 5061 to connect to SIP servers and other SIP endpoints. Port 5060 is commonly used for non-encrypted signaling traffic whereas port 5061 is typically used for traffic encrypted with TLS. SIP is primarily used in setting up and tearing down voice or video calls.
SIP Requests
INVITE – A client is being invited to participate in a call.
ACK – The client has confirmed the INVITE request.
BYE – The call has been terminated by either the caller or callee.
CANCEL – Cancel any pending requests.
OPTIONS – Queries the server for its capabilities.
REGISTER – Registers the client with the server according to the address in the To header.
PRACK – Similar to ACK, but a provisional confirmation.
SUBSCRIBE – Subscribes the device for an event notification.
NOTIFY – Notifies all subscribers of an event.
PUBLISH – Publishes an event to a server.
INFO – Sends information in the middle of a session that doesn’t modify the session’s state.
REFER – Asks the client to issue a SIP request, typically a call transfer.
MESSAGE – Sends an instant message using SIP.
UPDATE – Modifies a session’s state without altering the dialog state.
And, a little about Asterisk and FreePBX:
Asterisk is a software implementation of a telephone private branch exchange (PBX). Like any PBX, it allows attached telephones to make calls to one another, and to connect to other telephone services, such as the public switched telephone network (PSTN) and Voice over Internet Protocol (VoIP) services.
FreePBX is an open source GUI that controls and manages Asterisk
I found an awesome tool suite for this challenge: SIPVicious
SIPVicious suite is a set of tools that can be used to audit SIP based VoIP systems. It currently consists of the folowing tools:
svmap – this is a sip scanner. Lists SIP devices found on an IP range
svwar – identifies active extensions on a PBX
svcrack – an online password cracker for SIP PBX
svreport – manages sessions and exports reports to various formats
svcrash – attempts to stop unauthorized svwar and svcrack scans
Let’s get started then!
1 2 3 4 | |
Now we also have the Asterisk version. Next, we need to find valid extensions (it took a while of trial and error to get meaningful information on this one):
1 2 3 4 5 6 7 8 9 10 11 12 | |
The -D option enables scanning for default extensions, and the -m option specifies a request method (INVITE indicates that a client is being invited to participate in a call session.)
If you read the VM description on VulnHub, you probably remember that it mentions an easy way to get root to the machine. I found an exploit for that in Metasploit, more info here: http://www.offensive-security.com/vulndev/freepbx-exploit-phone-home/
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 | |
I specified the extension to match one of those that we previously discovered. And the machine belongs to us now!
1 2 3 4 5 6 7 8 9 | |
But we are not done. We still have to find the usernames and passwords, and get the voicemail from the Support account. I googled a bit for a helpful configuration file, which turned out to be the amportal.conf file:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 | |
We have the username and password for the admin interface now.
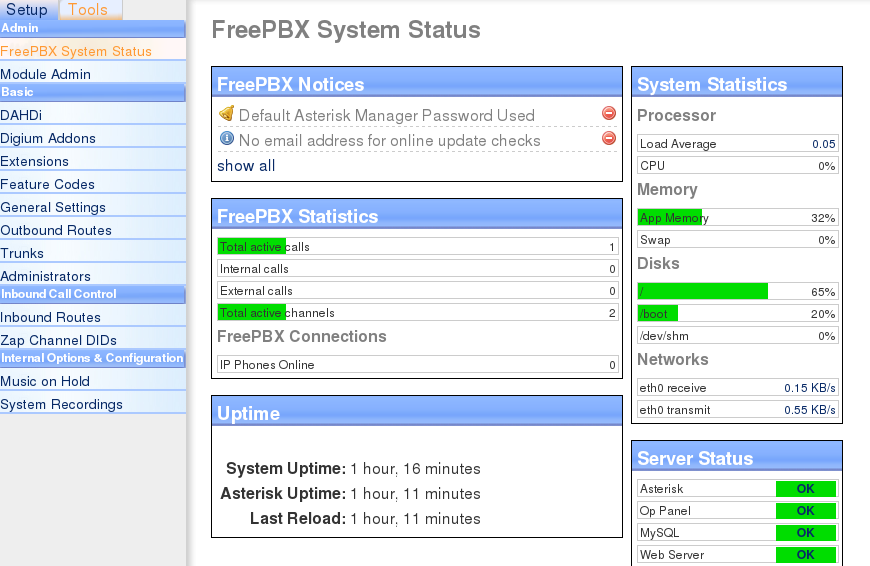
If we go to Panel, we can see that 2000 is the extension for the Support account. But I still couldn’t find a way to actually listen to the voicemail message, and I don’t have the password. But, I also have the credentials for the Asterisk Login Manager, so let’s see if that helps. To login and authenticate to the manager, you must send a “login” action, with your user name and secret (password) as parameters. We can use telnet for this (don’t forget to hit Enter twice after inputting the parameters):
1 2 3 4 5 6 7 8 9 10 11 | |
For a comprehensive list of Asterisk commands, check out this Asterisk CLI resource and Manager Actions. To list the SIP users, we have to use a “command” action this time. And then specify the command, which is sip show users:
1 2 3 4 5 6 7 8 9 10 11 12 13 | |
And it was this easy to get the usernames and passwords! I should have started with that! Now it’s possible to dial the extension and listen to the voicemail message. I just randomly chose Jitsi as a VoIP client for this task. You have to download and install the package file:
1 2 | |
Next, create an account in Jitsi:
However, when you make the call, it asks for a voicemail password! I went back to my shell on the machine and to googling about Asterisk voicemail paswords. The configuration file that comes to the rescue is /etc/asterisk/voicemail.conf.
1 2 3 4 5 6 7 | |
So, the password is 0000, and we can now listen to the message, which I’ll type here for the sake of completeness (hope I got it right):
“Hey Mark, I think the support web access account has been compromised. I have changed the password to securesupport123, all one word in lowercase. You can log on at the usual address. See you in the morning”
Well, I really liked this challenge! It made me read up about various subjects I wasn’t familiar with, like Asterisk and SIP. I also discovered the SIPVicious suite, which should come in handy from now on. And it was a great feeling to finally hear the message at the end. Also, VoIP hacking is a very interesting topic, and I hope there will be more chances to practice and learn about it.
FORTUNE PROVIDES QUESTIONS FOR THE GREAT ANSWERS: #31
Q: What is the name of the world’s oldest kamikaze pilot?
A: Chicken Teriyaki.