Mission statement
Get root and read the contents of the file ‘key.txt’ in the root directory.
Recon
I started with a port scan of the target, but only the 80 port is open:
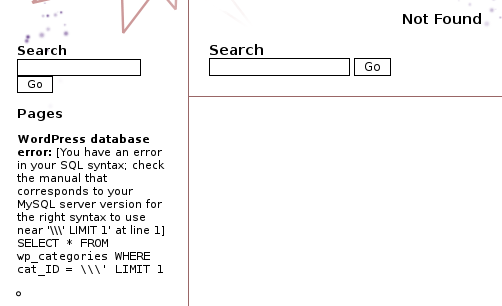
I looked at the links and noticed the URL for the post is http://192.168.80.162/Hackademic_RTB1/?p=9 and for the archives is http://192.168.80.162/Hackademic_RTB1/?cat=1 . Before going to Sqlmap, I manually inserted quotes in the URLs and sure enough, a SQL error for the cat parameter:
Exploit
Next I enumerated the databases with Sqlmap:
1 2 3 4 5 | |
Since this is a web-based challenge, I proceeded to look into the wordpress database:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 | |
I further enumerated the wp_users table and here I am showing only the relevant information:
1 2 3 4 5 6 7 | |
Cracking the hashes revealed the passwords of all the users:
1 2 3 4 5 6 | |
Then I went to the Wordpress login page at http://192.168.80.162/Hackademic_RTB1/wp-login.php and logged in as NickJames (assumed he was admin because of his password). But there was nothing extraordinary to be done with his privileges, just adding and editing posts. We have more users to try though! When I reached GeorgeMiller, I noticed there were more actions available in the admin panel:
In the Presentation tab I could edit themes for the site. I picked the 404.php file and replaced its content with a line that would echo something first, so I don’t waste my time with shells without checking if code is executed successfully.
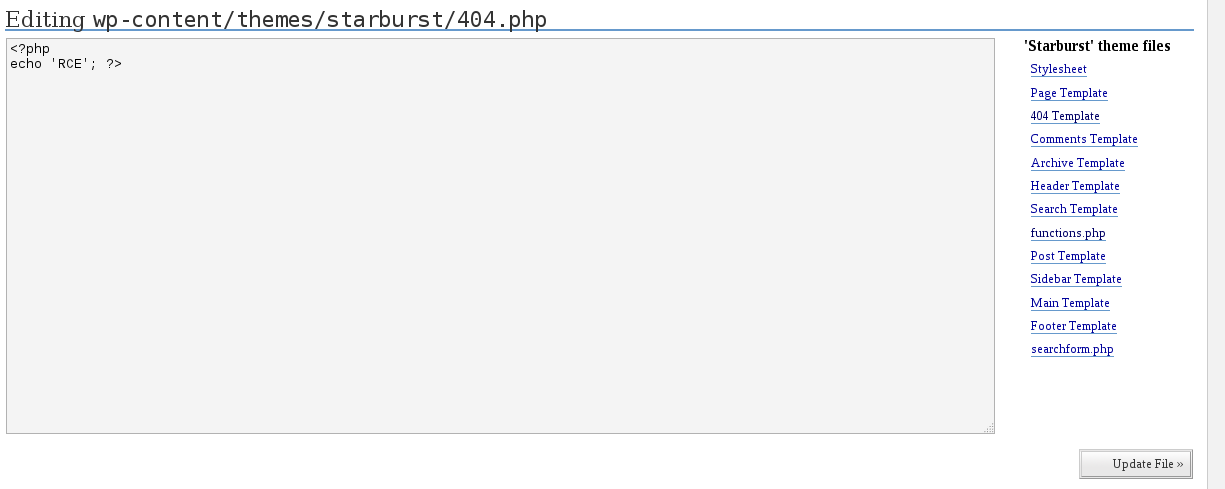
When I went to the http://192.168.80.162/Hackademic_RTB1/wp-content/themes/starburst/404.php URL, I saw RCE displayed, so next I used the now-familiar reverse PHP shell from pentestmonkey. Set up my listener and visited the URL again to receive the shell:
1 2 3 4 5 6 7 8 | |
Privilege escalation
The shell kept echoing back the commands I was running but otherwise it worked fine. I didn’t find anything interesting that I could use during local enumeration, so I then searched for privilege escalation exploits that might apply to the kernel version 2.6.31 found on the box. The exploit that worked was the RDS privilege escalation exploit by Dan Rosenberg. You can also find it on Kali with Searchsploit. I compiled it on my machine with the -m32 flag for the target architecture and transfered it via netcat. Then I ran it and I stared a bit at the blinking cursor before confirming that it gave me root:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 | |
Debriefing
The machine looked pretty tightly locked with only a web server running. But the WordPress version was contained a known SQLi exploit that handed down the hashes for the users. One user had the rights to upload code on the server and facilitated geting (limited) access on the target. The kernel was vulnerable to a local root exploit, and from there it was game over.
GG, nice VM! Now let’s end with some wisdom straight from the cow’s mouth:
1 2 3 4 5 6 7 8 | |