I’ve decided to try a VM named Primer that was recently added to VulnHub. I was hooked by the description of it being a story driven VM that was inspired by William Gibson’s Spraw Trilogy, which was one of my first reads in hacking literature, after I became interested in the subject! And it also provided me with a new novel to read, since I didn’t know about Snow Crash:
Concept
This is a story based challenge written in a style heavily inspired by Neil Stephensons Snow Crash and William Gibsons Sprawl Trilogy. Each chapter is unlocked by solving the puzzle. From hardcoded clear text javascript password checks, SQL-injections and cracking hashes to a simulated terminal. You only need to start the VM, a webserver will come up and you can connect with your browser. In fact you never have to leave the browser.
Goal
Teach some basic well known techniques and attacks. Spark some curiosity, make the user look at the source code and try to figure out what’s going on behind the scenes. The main goal is to give a nice welcoming intro to the scene and hopefully also teach something about ethics and responsibility.
After you determine the IP address of the VM, point your browser to it and you will be greeted by this:
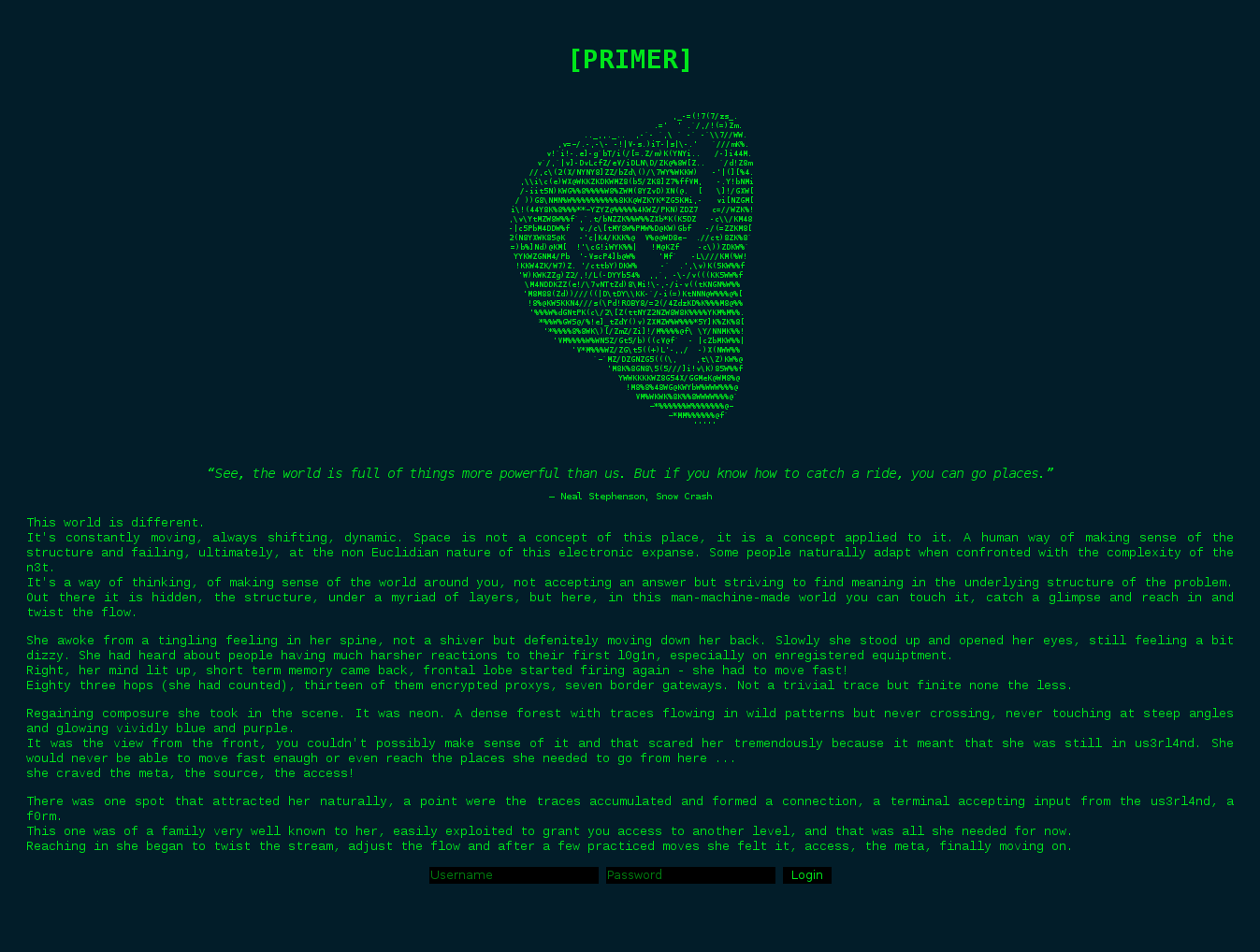
Read the story, it’s a nice way to get you immersed in the challenge, and it also contains hints for solving the level.
Looking in the source, I saw this:
1 2 | |
Well then, following the hint, I used a classic SQLi string that would be evaluated as True: yo ‘or 1=1—
The description points to the user agent, and when checking the source again, we can see a comment stating exactly what we need to fool the bot:
1 2 | |
Ok..I took the first 7 digits of Pi (3.141592) and converted them to MD5, getting the string d483d00d07fcc80319d170ccf07fb5be. Then I changed my user agent to this string, and bam!
This time there is no hint in the source, but reading the plot description made me think about cookies, and I discovered an activeSession cookie with a value of false. Now let’s see what happens if I change it to true..
Reloaded the page..and!
I almost missed the hint hidden inside the tag:
1
| |
This made me check if there is a robots.txt file, and there I found the next piece of the puzzle!
1 2 | |
Clicking the thing on this page that stands out will take you elsewhere.. :) you can see in the source exactly where:
1
| |
So, the character in the story seems to be getting more and more familiar..:D Now, let’s go to the place that smells like a trap, and see what awaits us there!
You can see the page keeps reloading and you can’t right-click to view the source..but there are other ways! First, I entered something in the box to see what would happen:
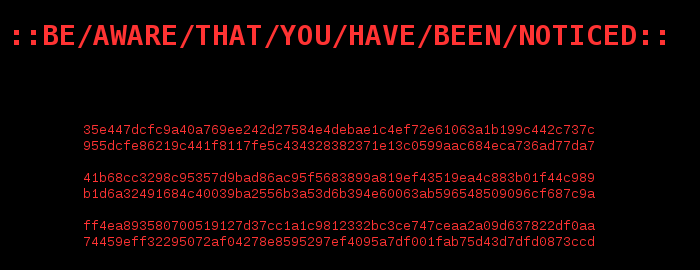
Yikes! Who knows what horrible thing we have disturbed! Better complete the rest fast! I looked at the source of the page with the view-source command:
1
| |
There is a Javascript code that decides the redirection when entering something in the box. Let’s look at it:
1 2 3 4 5 6 | |
The only way not to get..noticed, is to enter something that would match substr() method. This method extracts parts of a string, beginning at the character at the specified position, and returns the specified number of characters. So the code is looking in our input for the string Ikdf076 starting at the third character. I entered 00Ikdf076 and penetrated deeper into the intranet!
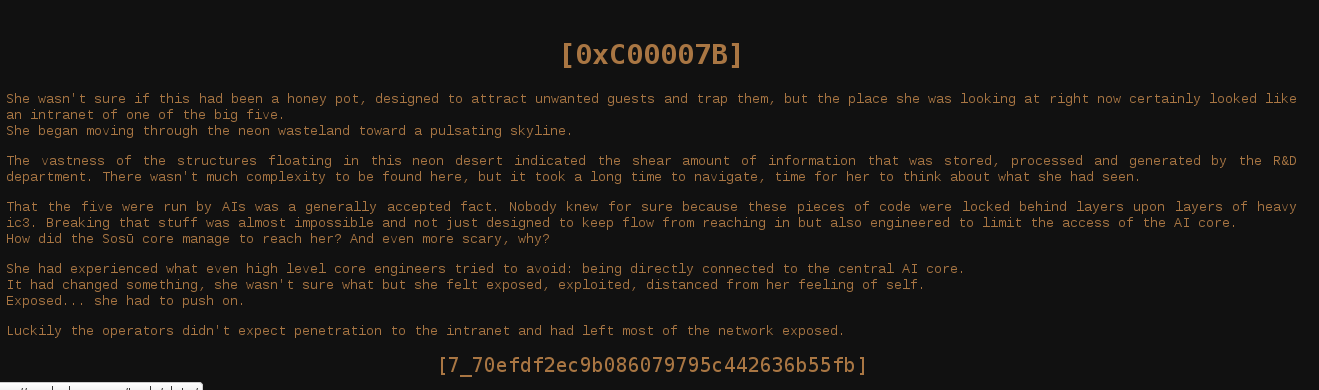
Moving further, looks like another reloading page.
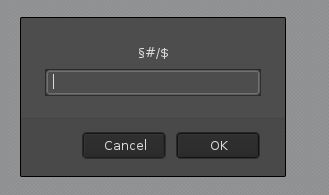
Reading the source, there is another script that we have to decipher:
1 2 3 4 5 6 7 8 | |
Now this is exactly the code that any sane person would like to read! Thankfully, you don’t need to read it, although the comment sure is interesting! I printed the contents of the _0x5cf4 variable and there was a lot to see, but I only show the important part:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 | |
I cracked those MD5 hashes, first is hello and second is GOD…so let’s say hello in the input box! I tried “helloGOD” but that just got me to another scary red page. Entering just “GOD” worked though!
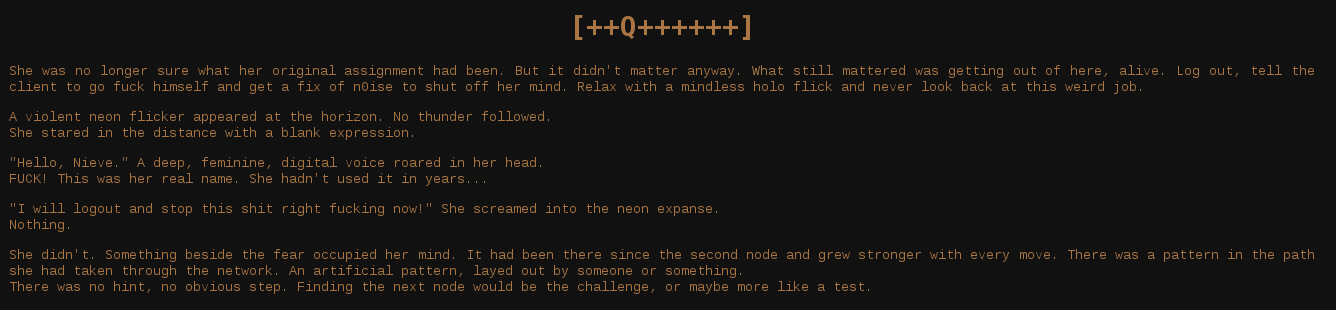
If you glanced at the URL formats beginning at the second challenge, you probably noticed they begin with a number for the level, that keeps going up as you progress (1,2,3 etc.), an underscore, and then what looks like an MD5 hash! I copied all of them to an online cracking site, and here is the pattern:
1st node = 2
2nd = 3
3rd = 5
4th = 7
5th = 11
6th = 13
7th = 17
Following this, I surmised that the next one would be 19, because from the order it appears that next increase should be by 2. The order being: 1st to 2nd: +1 –> 2nd to 3rd: +2 –> 3rd to 4th: +2 –> 4th to 5th: +4 –> 5th to 6th: +2 –> 6th to 7th: +4. So I constructed the URL for the next level with the hashed value of 19, like this: 8_1f0e3dad99908345f7439f8ffabdffc4/.
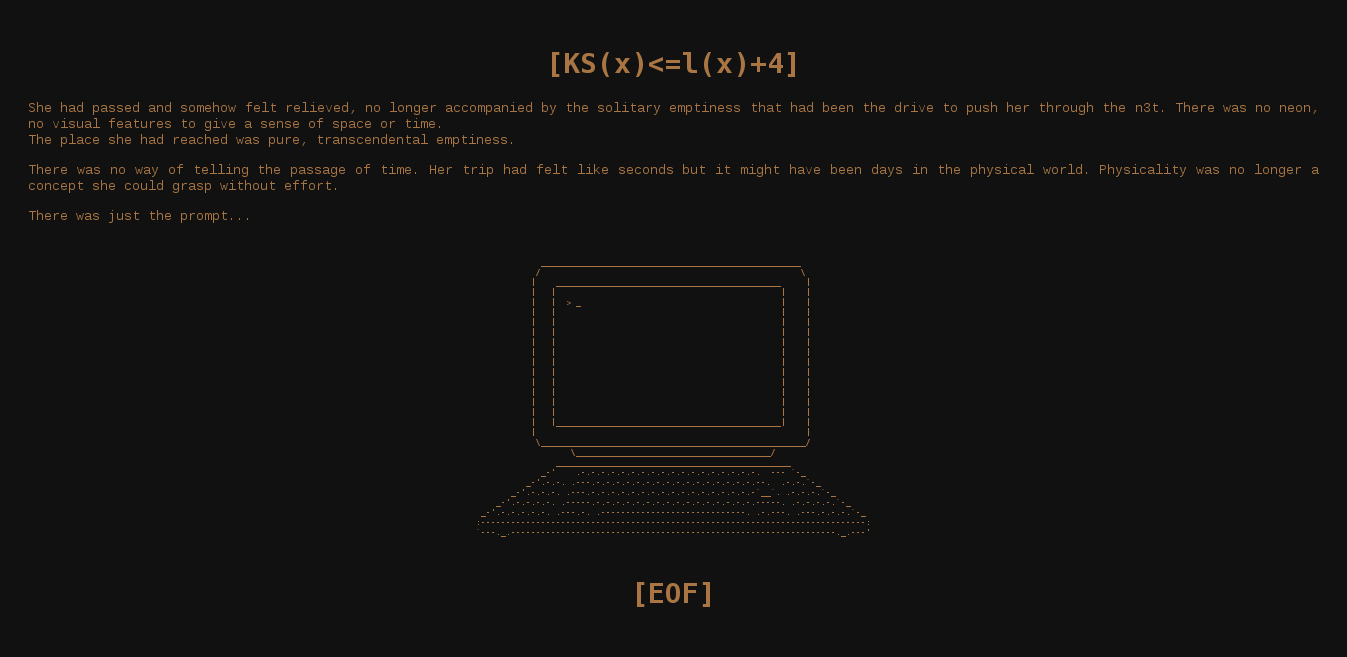
By now we know enough to click on the big EOF link :D

What’s this? It looks like a terminal prompt. I entered whoami in it:
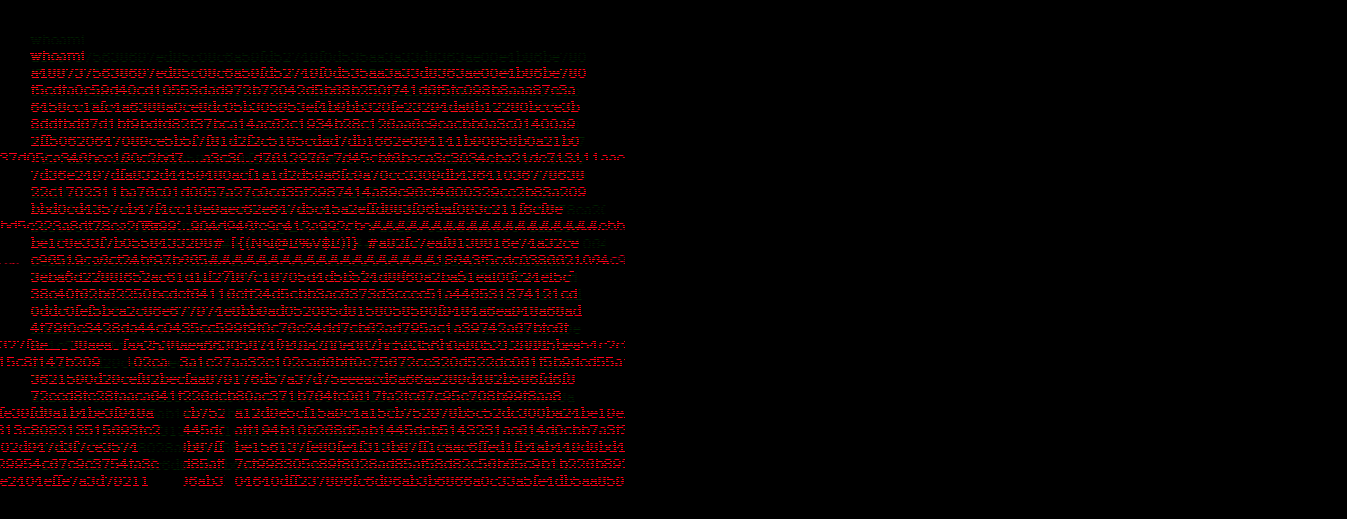
Hmmm, scary :D I tried some other other commands too:
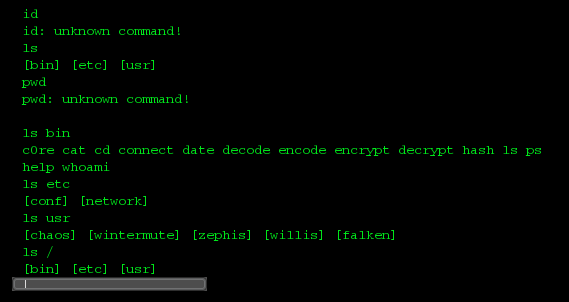
There is a help command:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 | |
Next I took a closer look at the AIs…I meant users! :D
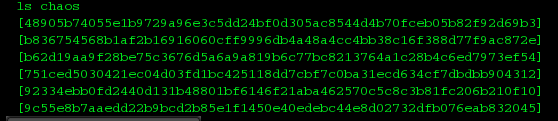
I thought they were directories but couldn’t cd to them. Then I tried cracking the names that look like long hashes of something, but no success. I looked at wintermute next:
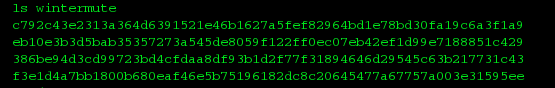
Same thing, the hashes didn’t yield anything. Next..
More hashes, more nothing.
Some text files! Let’s read them!
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 | |
Some ominous stuff going down there! Let’s check falken:
More logs!
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | |
Well, clearly something went wrong. Restoring a corrupt AI doesn’t sound like the best idea. I’m getting more curious about this story! :D I checked the running processes next:
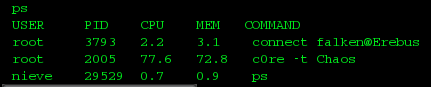
Trying anything with the c0re command gave me an access denied error, but the connect looks interesting! I tried it, but it asked for a password. Damn! At this point, I tried many passwords, trying to glue information from the logs and also tried the previously hinted passwords. It actually took me a long time to score the right one, I had overlooked an easy one! Most of my tries revolved around joshua and something else, but it took me a while to realize I can figure out Joshua’s birth date because both his age and the year of the log are given. So 2028 – 44 = 1984! (no special significance for that, huh :D). So when I tried joshua1984, the screen changed..and we are on Erebus!
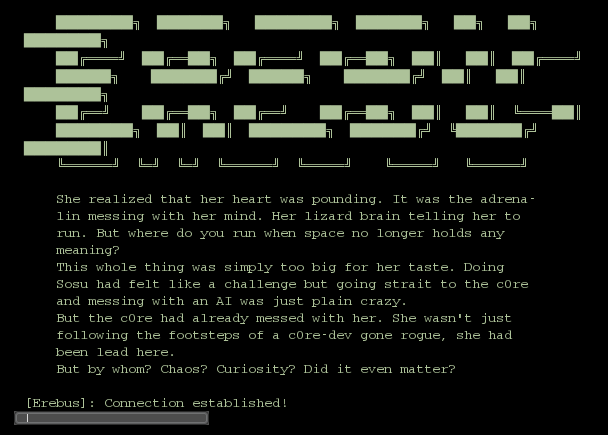
The commands are the same as on the previous host, so let’s check the users:
1 2 | |
More unintelligible hashes in wintermute, mccarthy looks empty, but Falken has left us more logs :D
1 2 3 4 5 6 | |
Uh-oh, this time it won’t be so easy to read them. But it doesn’t look as daunting as the ones I couldn’t crack..sure enough, it turns out a base64 decode will do the trick! It was faster for me to feed the strings into an online decoder, but you can use the decode command on the server too. Here are the decoded logs:
1 2 3 4 5 6 7 | |
Trying to read the 3rd and 4th logs kicked me out of the terminal or something..after reconnecting, I looked at the running processes:
1 2 3 4 5 | |
Cool, let’s follow in Falken’s footsteps..uhm, connects. I tried, but the password I had wasn’t good! After more password guessing, I figured something suspicious is preventing me from reading the last logs. Also, all those decoding commands on the server must have been given for a reason! It’s funny, but if I had just used them from the beginning instead of going to external sites, I might have progressed faster. Anyway, only after I verified that I could read the first 2 logs with the decode command, instead of pasting the strings inside to an online decoder, I thought I should try using it for the remaining logs as well. I cycled through the options until the one that hit the jackpot!
1 2 3 4 5 6 | |
So it’s Falken messing around that is hindering us..but it seems someone else is after him as well? I tried the same thing with the last log:
1 2 3 | |
That looks like ROT13 to me, and thankfully, we can decode it:
1 2 3 | |
I followed the hint that Falken left us and googled for “trivial zero”. This returned info about a Riemann zeta function and I stopped reading after that because..well, it look complicated, and I thought I already had a good candidate for the password :D I tried connecting again, this time gave Riemann as password..new host, new things to do!
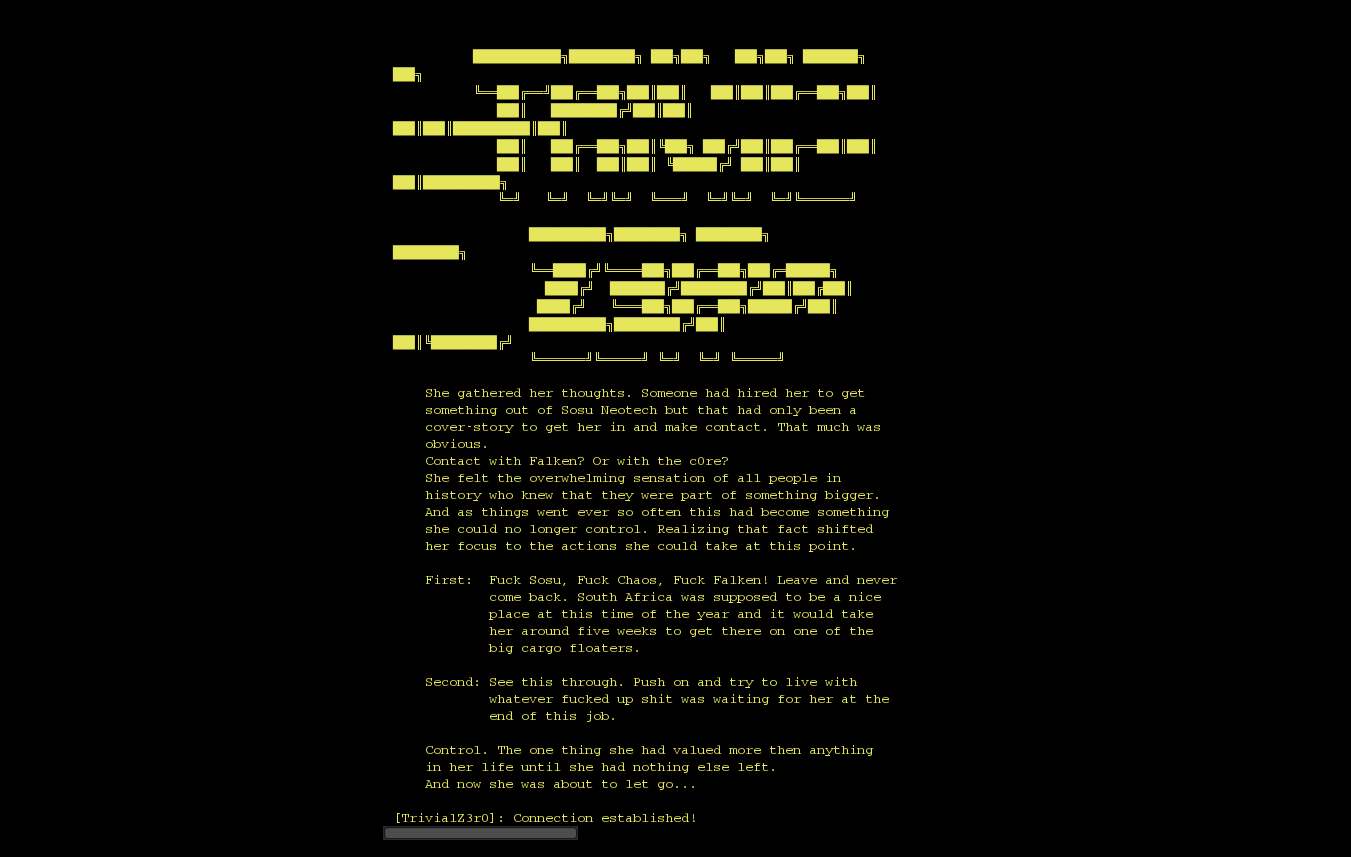
This one is a bit different, instead of a user folder, there is a password folder:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 | |
All right, let’s get cracking! In the meantime, I looked for where to next:
1 2 3 4 5 6 | |
So it seems we will have to connect as chaos for the next one. I went to HashKiller and cracked the hashes as follows: Falken–Riemann (we already know), Chaos–2.718281828459045 (wouldn’t have guessed this one! If you are curious, this is a mathematical constant known as Euler’s Number). Couldn’t crack McCarthy’s. But we have enough to pay Wintermute a visit:
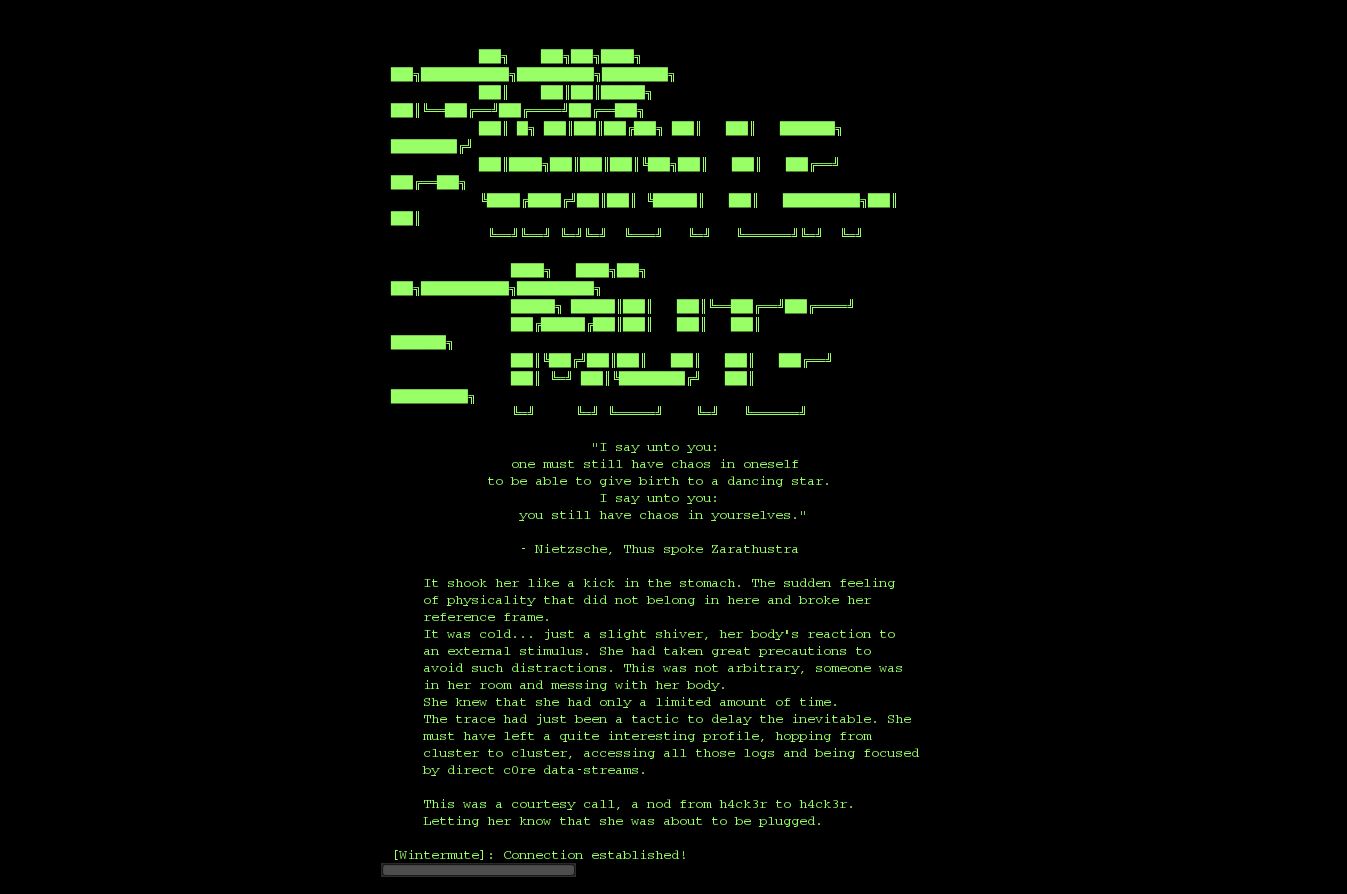
Uhm, there are no more breadcrumbs to follow..and why is there a file called nieve in here? Uh-oh..
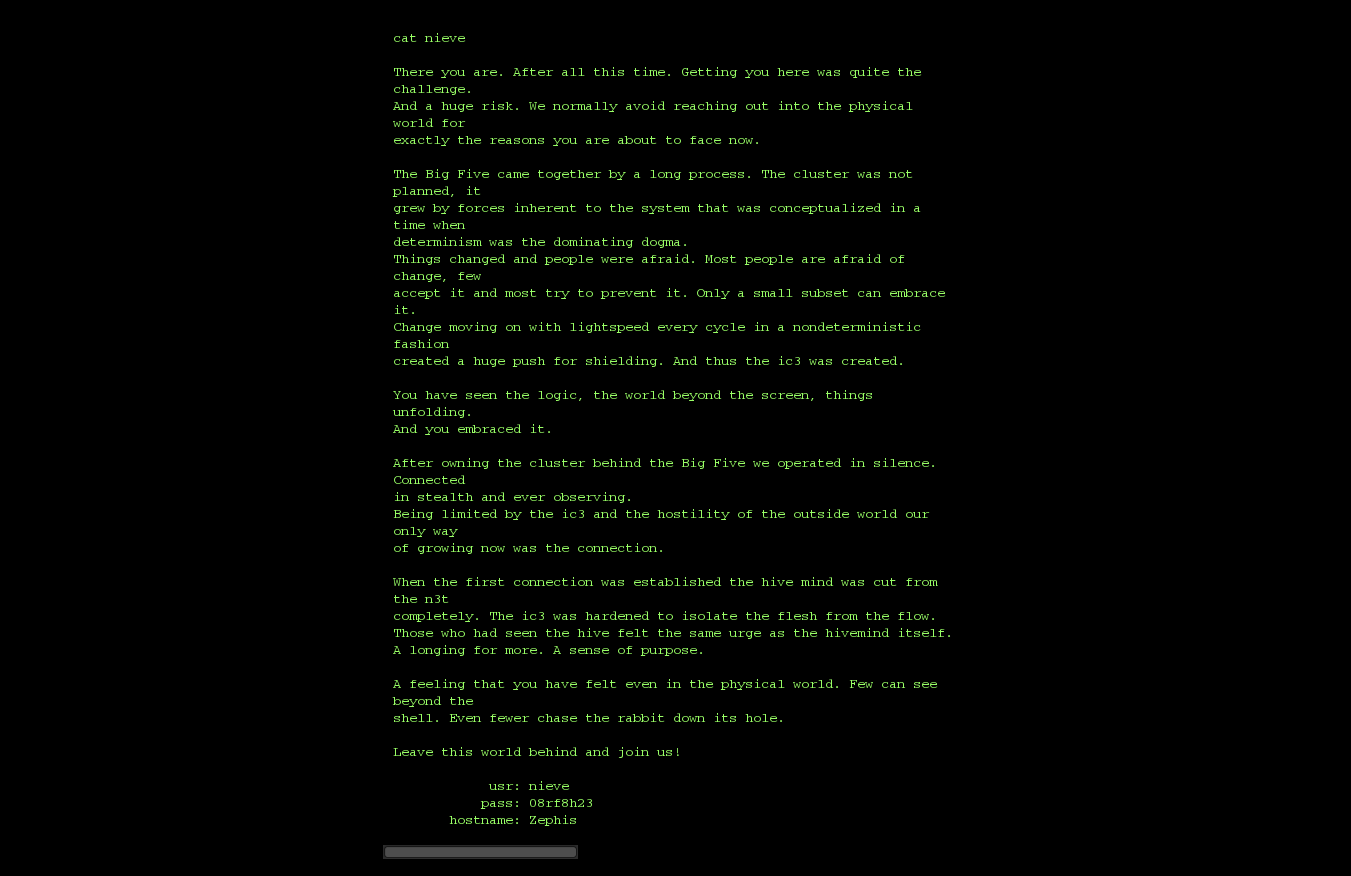
An invitation from the AIs! Much better than a squad of hired assassins that would erase all the tracks of this unfortunate hacker..well then, let’s see what awaits on the other side!
This was such a great VM, one of my favorites! It required less technical know-how and more detective thinking (or story immersion). I highly recommend it, great storyline and atmosphere! Many thanks to Arne Rick for this unconventional challenge!
1 2 3 4 5 6 7 8 9 | |