BeEF XSS Framework
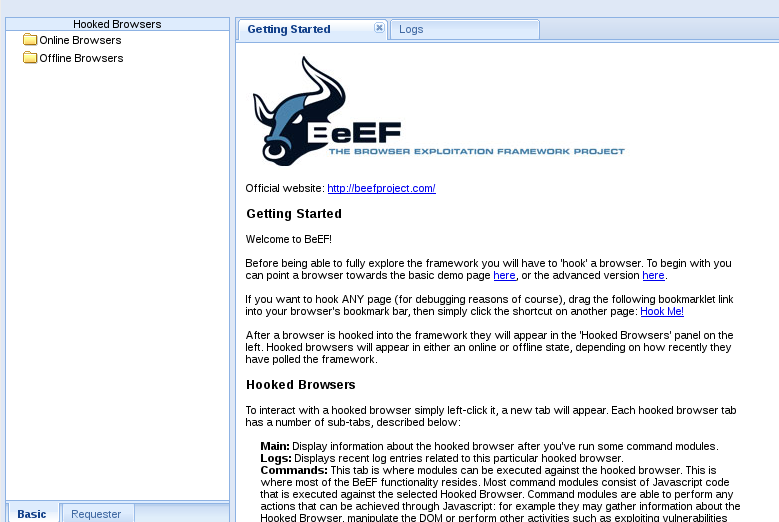
beef
BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser.
Amid growing concerns about web-borne attacks against clients, including mobile clients, BeEF allows the professional penetration tester to assess the actual security posture of a target environment by using client-side attack vectors. Unlike other security frameworks, BeEF looks past the hardened network perimeter and client system, and examines exploitability within the context of the one open door: the web browser. BeEF will hook one or more web browsers and use them as beachheads for launching directed command modules and further attacks against the system from within the browser context.
Exploit Database
searchsploit
Exploit Database Archive Search
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | |
Exploit Development Tools
edb-debugger
A Linux equivalent of the famous Olly debugger on the Windows platform. Some of its features are:
Intuitive GUI interface
The usual debugging operations (step-into/step-over/run/break)
Conditional breakpoints
Debugging core is implemented as a plugin so people can have drop in replacements. Of course if a given platform has several debugging APIs available, then you may have a plugin that implements any of them.
Basic instruction analysis
View/Dump memory regions
Effective address inspection
The data dump view is tabbed, allowing you to have several views of memory open at the same time and quickly switch between them.
Importing and generation of symbol maps
Plugins
NASM shell
This tool provides an easy way to see what opcodes are associated with certain x86 instructions by making use of nasm if it is installed and reachable through the PATH environment variable.
ollydbg
OllyDbg is a 32-bit assembler level analysing debugger for Microsoft Windows. Emphasis on binary code analysis makes it particularly useful in cases where source is unavailable.
Features:
Intuitive user interface, no cryptical commands
Code analysis – traces registers, recognizes procedures, loops, API calls, switches, tables, constants and strings
Directly loads and debugs DLLs
Object file scanning – locates routines from object files and libraries
Allows for user-defined labels, comments and function descriptions
Understands debugging information in Borland® format
Saves patches between sessions, writes them back to executable file and updates fixups
Open architecture – many third-party plugins are available
No installation – no trash in registry or system directories
Debugs multithread applications
Attaches to running programs
Configurable disassembler, supports both MASM and IDEAL formats
MMX, 3DNow! and SSE data types and instructions, including Athlon extensions
Full UNICODE support
Dynamically recognizes ASCII and UNICODE strings – also in Delphi format!
Recognizes complex code constructs, like call to jump to procedure
Decodes calls to more than 1900 standard API and 400 C functions
Gives context-sensitive help on API functions from external help file
Sets conditional, logging, memory and hardware breakpoints
Traces program execution, logs arguments of known functions
Shows fixups
Dynamically traces stack frames
Searches for imprecise commands and masked binary sequences
Searches whole allocated memory
Finds references to constant or address range
Examines and modifies memory, sets breakpoints and pauses program on-the-fly
Assembles commands into the shortest binary form
Starts from the floppy disk
pattern create
Generate a string composed of unique patterns
1 2 | |
pattern offset
Find the offset in an exploit string where your address to overwrite EIP should be
1 2 3 | |
Metasploit
World’s most used penetration testing software…the hacker’s best friend. No further description needed
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 | |
Network Exploitation
armitage
Armitage is a scriptable red team collaboration tool for Metasploit that visualizes targets, recommends exploits, and exposes the advanced post-exploitation features in the framework.
Through one Metasploit instance, your team will:
Use the same sessions
Share hosts, captured data, and downloaded files
Communicate through a shared event log.
Run bots to automate red team tasks.
Armitage organizes Metasploit’s capabilities around the hacking process. There are features for discovery, access, post-exploitation, and maneuver.
exploit6
Performs exploits of various CVE known IPv6 vulnerabilities on the destination
1 2 3 4 5 6 7 | |
ikat
iKAT is designed to provide access to the underlying operating system of a Kiosk terminal by invoking native OS functionality.
jboss-autopwn
This JBoss script deploys a JSP shell on the target JBoss AS server. Once deployed, the script uses its upload and command execution capability to provide an interactive session.
Features include:
Multiplatform support – tested on Windows, Linux and Mac targets
Support for bind and reverse bind shells
Meterpreter shells and VNC support for Windows targets
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 | |
termineter
Termineter is a framework written in python to provide a platform for the security testing of smart meters. It implements the C12.18 and C12.19 protocols for communication. Currently supported are Meters using C12.19 with 7-bit character sets. Termineter communicates with Smart Meters via a connection using an ANSI type-2 optical probe with a serial interface.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 | |
Social Engineering Toolkit
The Social-Engineer Toolkit is an open-source penetration testing framework designed for Social-Engineering. SET has a number of custom attack vectors that allow you to make a believable attack in a fraction of the time.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 | |