PentesterAcademy has a section dedicated to web application security challenges. In this post I will present my solution to the first challenge, which requires form bruteforcing to authenticate on the provided web page:
http://pentesteracademylab.appspot.com/lab/webapp/1
This is how the page looks like:
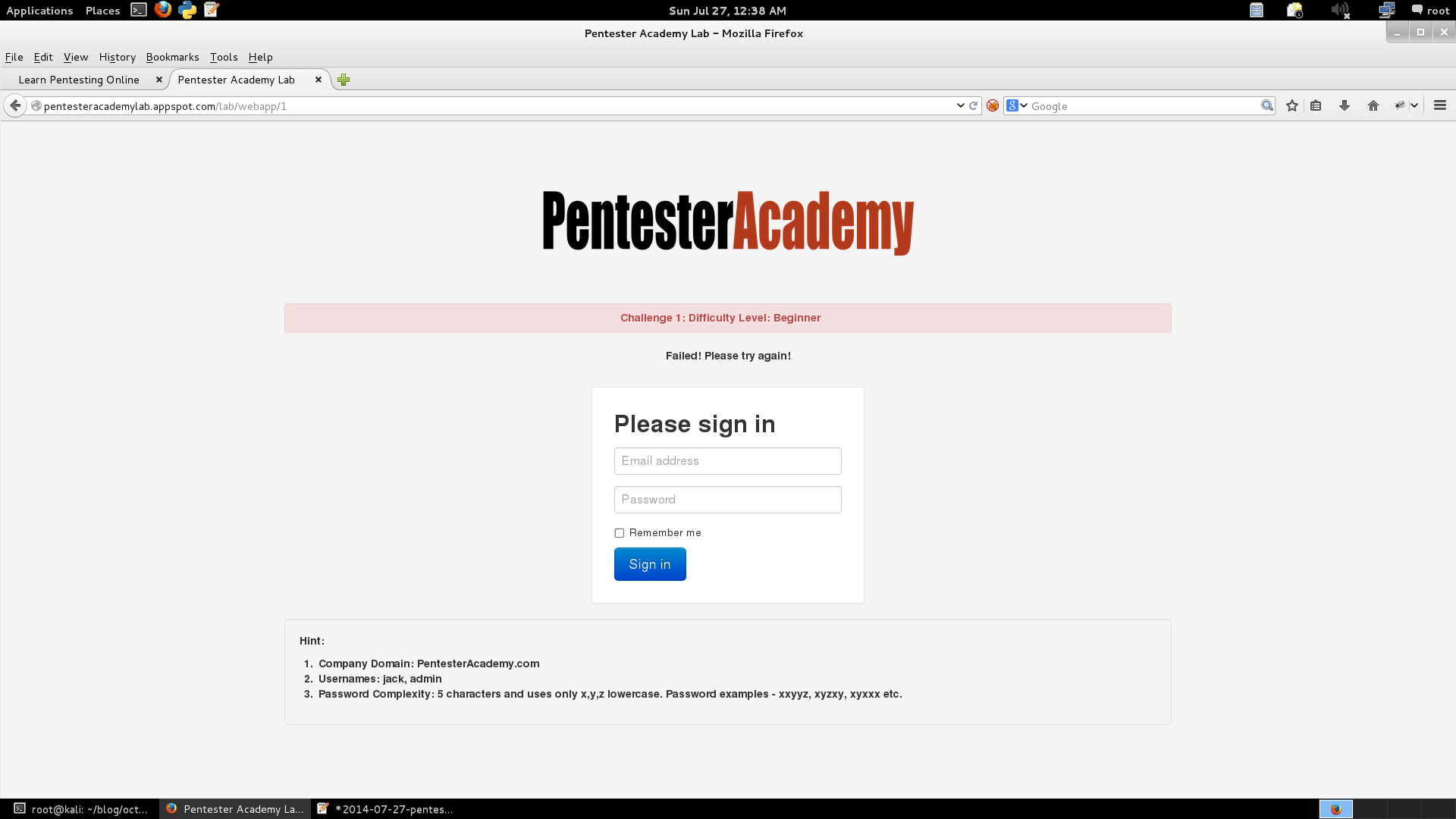
The provided hint should help with writing a bruteforce script:
Hint:
Company Domain: PentesterAcademy.com
Usernames: jack, admin
Password Complexity: 5 characters and uses only x,y,z lowercase. Password examples – xxyyz, xyzxy, xyxxx etc.
So, what we need here is to test the login with usernames of the form user@companydomain and 5 character passwords constructed from the given characters.
I wrote a Python script to do that:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 | |
I used the requests module, which is very handy for all sorts of URL interaction. To figure out the parameter names and how are they passed to the login form, I tested with some garbage values and saw the URL looked like this:
1
| |
From that I knew to use the GET request in the code. Also, when you fail, you get a message stating that you should try again, so I looked for that in the response from the server, and I concluded that if it were absent, it means that the login was successful. When you complete the challenge, there is also a message that says “Well done! This challenge has been cracked!”
Here is a snippet of the output:
1 2 3 4 5 6 | |
Today’s fortune cookie:
While you recently had your problems on the run, they’ve regrouped and are making another attack.