Kali is an awesome distribution for pentesting. But with so many choices, one may find it daunting to find a specific tool for a task without having used it before. Or maybe you’re wondering about some tools but don’t feel like testing every single one. So I decided to briefly go over the tools provided by Kali and provide a quick description. Where available, I will use the ones presented on their respective websites / manpages etc.
So, let’s begin!
DNS Analysis
dnsdict6
Enumerates a domain for DNS entries, it uses a dictionary file if supplied or a built-in list otherwise. This tool is based on dnsmap by gnucitizen.org.
dnsenum
Multithreaded perl script to enumerate DNS information of a domain and to discover non-contiguous ip blocks.
dnsmap
dnsmap is mainly meant to be used by pentesters during the informatio ngathering/enumeration phase of infrastructure security assessments. During the enumeration stage, the security consultant would typically discover the target company’s IP netblocks, domain names, phone numbers, etc …
Subdomain brute-forcing is another technique that should be used in the enumeration stage, as it’s especially useful when other domain enumeration techniques such as zone transfers don’t work (I rarely see zone transfers being publicly allowed these days by the way).
dnsrecon
DNS Enumueration and Scanning Tool
The script will perform the following:
Standard Record Enumeration for a given domain (A, NS, SOA and MX).
Top Leven Domain Expansion for a given domain.
Zone Transfer against all NS records of a given domain.
Reverse Lookup against a given IP Range given a start and end IP.
SRV Record enumeration
Brute force hostnames and subdomains of a given target domain using a wordlist.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 | |
dnsrevenum6
Performs a fast reverse DNS enumeration and is able to cope with slow servers.
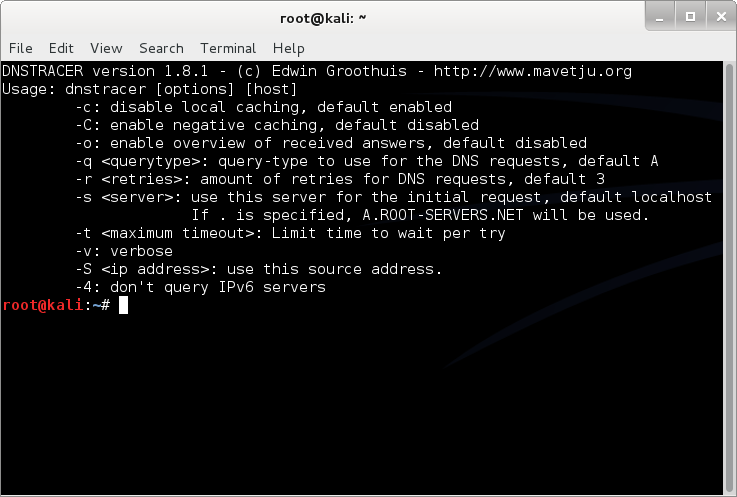
dnstracer
Determines where a given Domain Name Server (DNS) gets its information from, and follows the chain of DNS servers back to the servers which know the data.
dnswalk
DNS debugger. It performs zone transfers of specified domains, and checks the database in numerous ways for internal consistency, as well as for correctness according to accepted practices with the Domain Name System.
fierce
Fierce is a semi-lightweight scanner that helps locate non-contiguous IP space and hostnames against specified domains. It’s really meant as a pre-cursor to nmap, unicornscan, nessus, nikto, etc, since all of those require that you already know what IP space you are looking for. This does not perform exploitation and does not scan the whole internet indiscriminately. It is meant specifically to locate likely targets both inside and outside a corporate network. Because it uses DNS primarily you will often find mis-configured networks that leak internal address space. That’s especially useful in targeted malware.
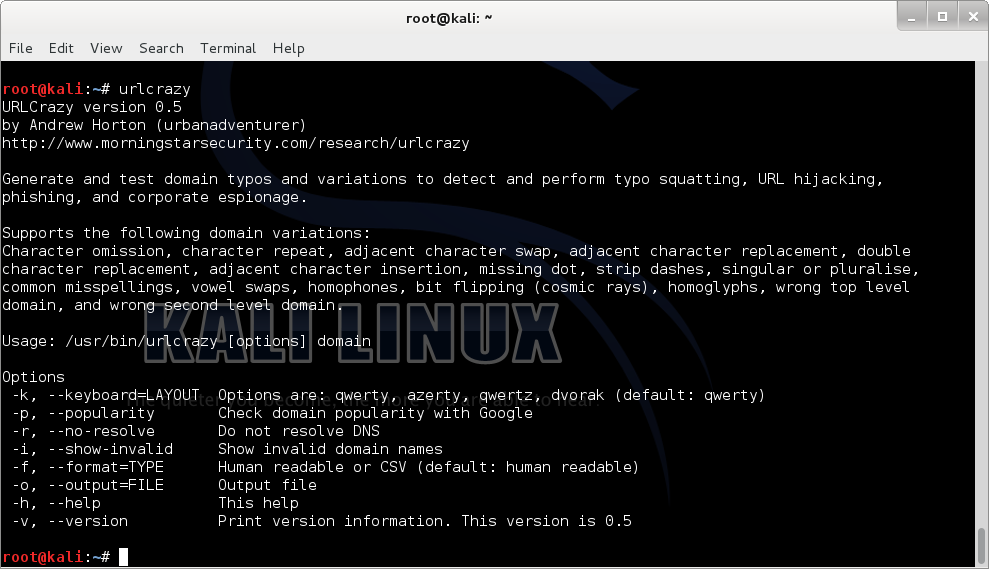
urlcrazy
Generate and test domain typos and variations to detect and perform typo squatting, URL hijacking, phishing, and corporate espionage.
IDS/IPS Identification
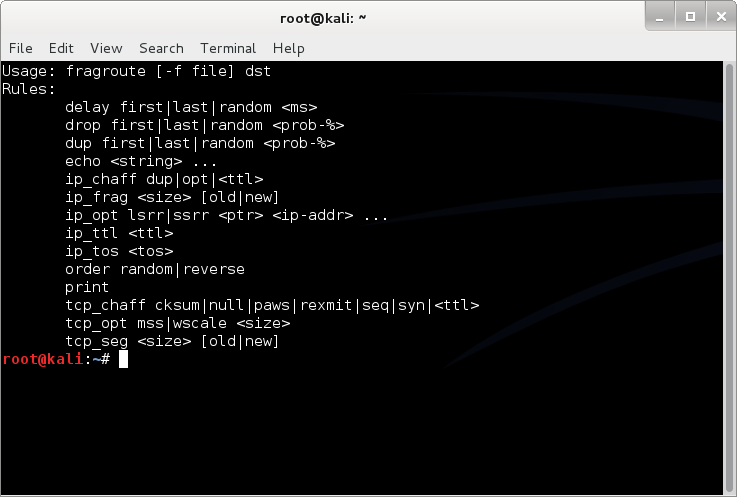
fragroute
intercept, modify, and rewrite egress traffic
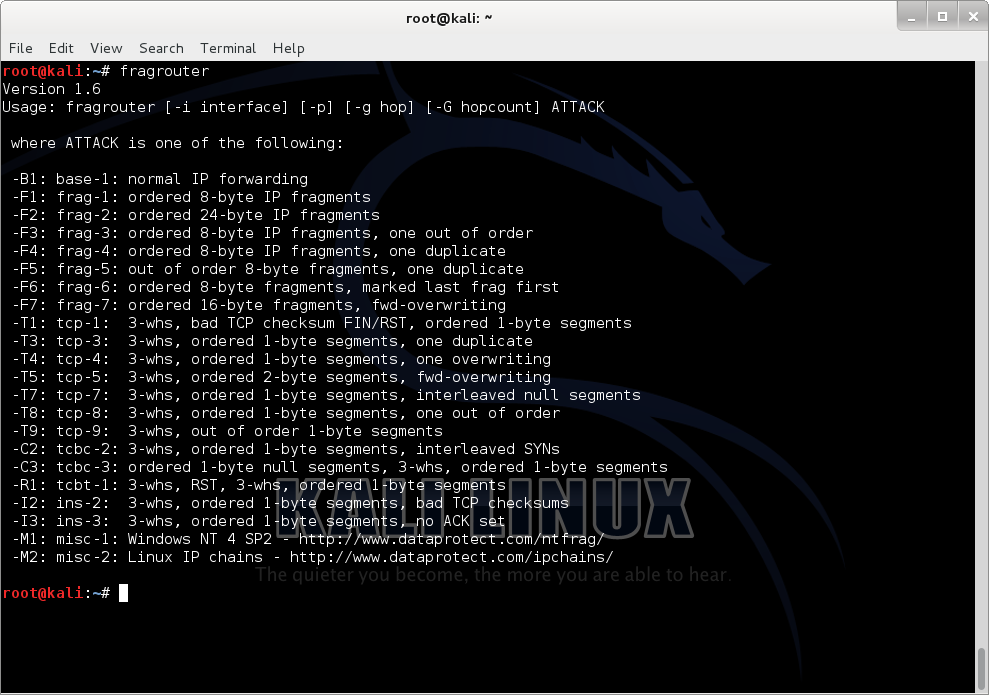
fragrouter
network intrusion detection evasion toolkit
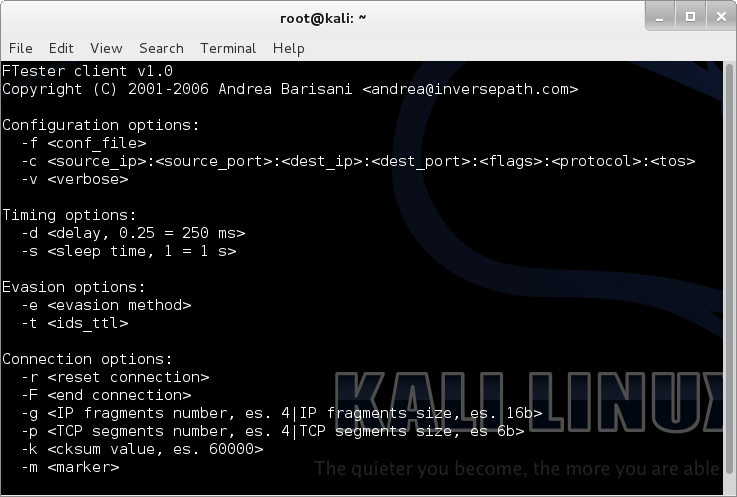
ftest
FTester is a tool designed for testing firewalls filtering policies and Intrusion Detection System (IDS) capabilities.
lbd
load balancing detector – Checks if a given domain uses load-balancing
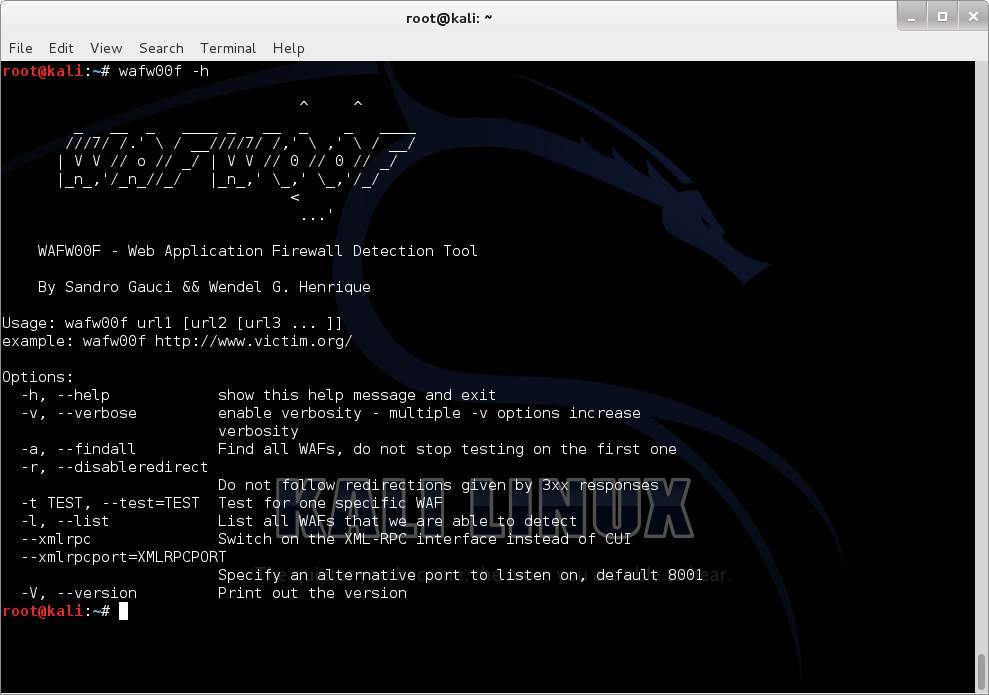
wafw00f
Web Application Firewall Detection Tool
Live Host Identification
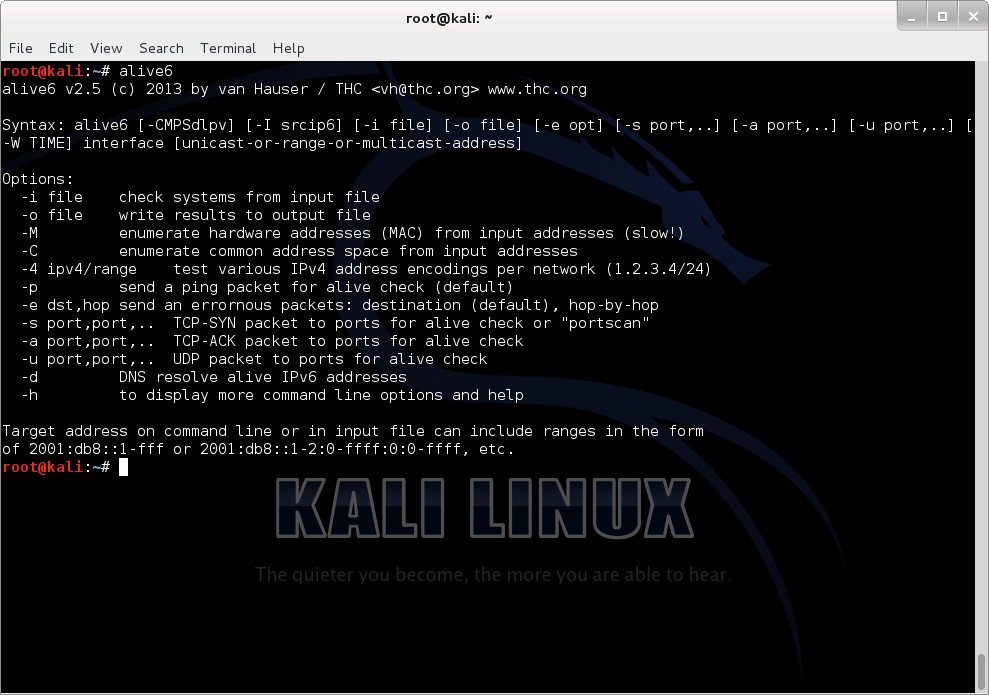
alive6
an effective alive scanner, which will detect all systems listening to this address
arping
sends ARP and/or ICMP requests to the specified host and displays the replies.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 | |
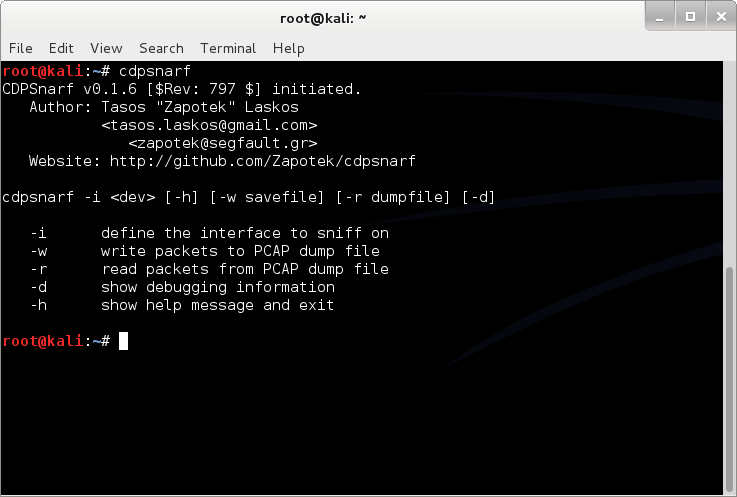
cdpsnarf
Cisco Discovery Protocol Sniffer
CDPSnarf is a network sniffer exclusively written to extract information from CDP packets. It provides all the information a “show cdp neighbors detail” command would return on a Cisco router and even more.
detect-new-ip6
This tool detects new IPv6 addresses joining the local network.
detect_sniffer6
Tests if systems on the local LAN are sniffing. Works against Windows, Linux, OS/X and *BSD If no target is given, the link-local-all-nodes address is used, which however not always works.
dmitry
DMitry (Deepmagic Information Gathering Tool) is a UNIX/(GNU)Linux command line application with the ability to gather as much information as possible about a host.
Basic functionality of DMitry allows for information to be gathered about a target host from a simple whois lookup on the target to uptime reports and TCP portscans.
The application is considered a tool to assist in information gathering when information is required quickly by removing the need to enter multiple commands and the timely process of searching through data from multiple sources.
dnmap-client & dnmap-server
dnmap is a framework to distribute nmap scans among several clients. It reads an already created file with nmap commands and send those commands to each client connected to it. The framework use a client/server architecture. The server knows what to do and the clients do it. All the logic and statistics are managed in the server. Nmap output is stored on both server and client. Usually you would want this if you have to scan a large group of hosts and you have several different internet connections (or friends that want to help you)
1 2 3 4 5 6 7 | |
1 2 3 4 5 6 7 8 9 10 11 12 13 | |
fping
send ICMP ECHO_REQUEST packets to network hosts
hping3
hping3 is a network tool able to send custom TCP/IP packets and to display target replies like ping program does with ICMP replies. hping3 handle fragmentation, arbitrary packets body and size and can be used in order to transfer files encapsulated under supported protocols. Using hping3 you are able to perform at least the following stuff:
- Test firewall rules
- Advanced port scanning
- Test net performance using different protocols, packet size, TOS (type of service) and fragmentation.
- Path MTU discovery
- Transferring files between even really fascist firewall rules.
- Traceroute-like under different protocols.
- Firewalk-like usage.
- Remote OS fingerprinting.
- TCP/IP stack auditing.
- A lot of others.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 | |
inverse_lookup6
Performs an inverse address query, to get the IPv6 addresses that are assigned to a MAC address. Note that only few systems support this yet.
miranda
Miranda can discover UPnP hosts either passively or actively, and all of a host’s reported devices types, services, actions and variables can be enumerated with a single command.
ncat
Ncat is a feature-packed networking utility which reads and writes data across networks from the command line. Ncat was written for the Nmap Project and is the culmination of the currently splintered family of Netcat incarnations. It is designed to be a reliable back-end tool to instantly provide network connectivity to other applications and users. Ncat will not only work with IPv4 and IPv6 but provides the user with a virtually limitless number of potential uses.
Among Ncat’s vast number of features there is the ability to chain Ncats together; redirection of TCP, UDP, and SCTP ports to other sites; SSL support; and proxy connections via SOCKS4 or HTTP proxies (with optional proxy authentication as well).
netdiscover
an active/passive arp reconnaissance tool.
passive_discovery6
Passivly sniffs the network and dump all client’s IPv6 addresses detected.
thcping6
Craft a ICMPv6/TCP/UDP packet with special IPv6 or EH header options.
wol-e
WOL-E is a suite of tools for the Wake on LAN feature of network attached computers, this is now enabled by default on many Apple computers. These tools include:
Bruteforcing the MAC address to wake up clients Sniffing WOL attempts on the network and saving them to disk Sniffing WOL passwords on the network and saving them to disk Waking up single clients (post sniffing attack) Scanning for Apple devices on the network for WOL enabling Sending bulk WOL requests to all detected Apple clients.
xprobe2
xprobe2 is an active operating system fingerprinting tool with a different approach to operating system fingerprinting. xprobe2 relies on fuzzy signature matching, probabilistic guesses, multiple matches simultaneously, and a signature database.
Network Scanners
nmap
Nmap (“Network Mapper”) is an open source tool for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. While Nmap is commonly used for security audits, many systems and network administrators find it useful for routine tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 | |
unicornscan
asynchronous network stimulus delivery/response recoring tool.
zenmap
Zenmap is a multi-platform graphical Nmap frontend and results viewer. Zenmap aims to make Nmap easy for beginners to use while giving experienced Nmap users advanced features. Frequently used scans can be saved as profiles to make them easy to run repeatedly. A command creator allows interactive creation of Nmap command lines. Scan results can be saved and viewed later. Saved scan results can be compared with one another to see how they differ. The results of recent scans are stored in a searchable database.
OS Fingerprinting
Covered in the above
OSINT Analysis
casefile
CaseFile is the little brother to Maltego. It targets a unique market of ‘offline’ analysts whose primary sources of information are not gained from the open-source intelligence side or can be programmatically queried. We see these people as investigators and analysts who are working ‘on the ground’, getting intelligence from other people in the team and building up an information map of their investigation.
CaseFile gives you the ability to quickly add, link and analyze data having the same graphing flexibility and performance as Maltego without the use of transforms.
creepy
creepy is an application that allows you to gather geolocation related information about users from social networking platforms and image hosting services. The information is presented in a map inside the application where all the retrieved data is shown accompanied with relevant information (i.e. what was posted from that specific location) to provide context to the presentation.
jigsaw
Email harvesting, can search on jigsaw.com
maltego
Maltego is a program that can be used to determine the relationships and real world links between:
People
Groups of people (social networks)
Companies
Organizations
Web sites
Internet infrastructure such as:
Domains
DNS names
Netblocks
IP addresses
Phrases
Affiliations
Documents and files
These entities are linked using open source intelligence.

metagoofil
Metagoofil is an information gathering tool designed for extracting metadata of public documents (pdf,doc,xls,ppt,docx,pptx,xlsx) belonging to a target company.
Metagoofil will perform a search in Google to identify and download the documents to local disk and then will extract the metadata with different libraries like Hachoir, PdfMiner? and others. With the results it will generate a report with usernames, software versions and servers or machine names that will help Penetration testers in the information gathering phase.

recon-ng
Recon-ng is a full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built in convenience functions, interactive help, and command completion, Recon-ng provides a powerful environment in which open source web-based reconnaissance can be conducted quickly and thoroughly.
theharvester
The objective of this program is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers and SHODAN computer database.
twofi
Twitter Words Of Interest
Build a custom wordlist based on Twitter keywords
Route analysis
0trace
Trace route to target
intrace
InTrace is a traceroute-like application that enables users to enumerate IP hops exploiting existing TCP connections, both initiated from local network (local system) or from remote hosts.
netmask
This program accepts and produces a variety of common network address and netmask formats. Not only can it convert address and netmask notations, but it will optimize the masks to generate the smallest list of rules. This is very handy if you’ve ever configured a firewall or router and some nasty network administrator before you decided that base 10 numbers were good places to start and end groups of machines.
trace6
A basic but very fast traceroute6 program. If no port is specified, ICMP6 Ping requests are used, otherwise TCP SYN packets to the specified port.
Service Fingerprinting
implementation6
Performs some IPv6 implementation checks, can be used to test some firewall features too. Takes approx. 2 minutes to complete.
implementation6d
Identifies test packets by the implementation6 tool, useful to check what packets passed a firewall
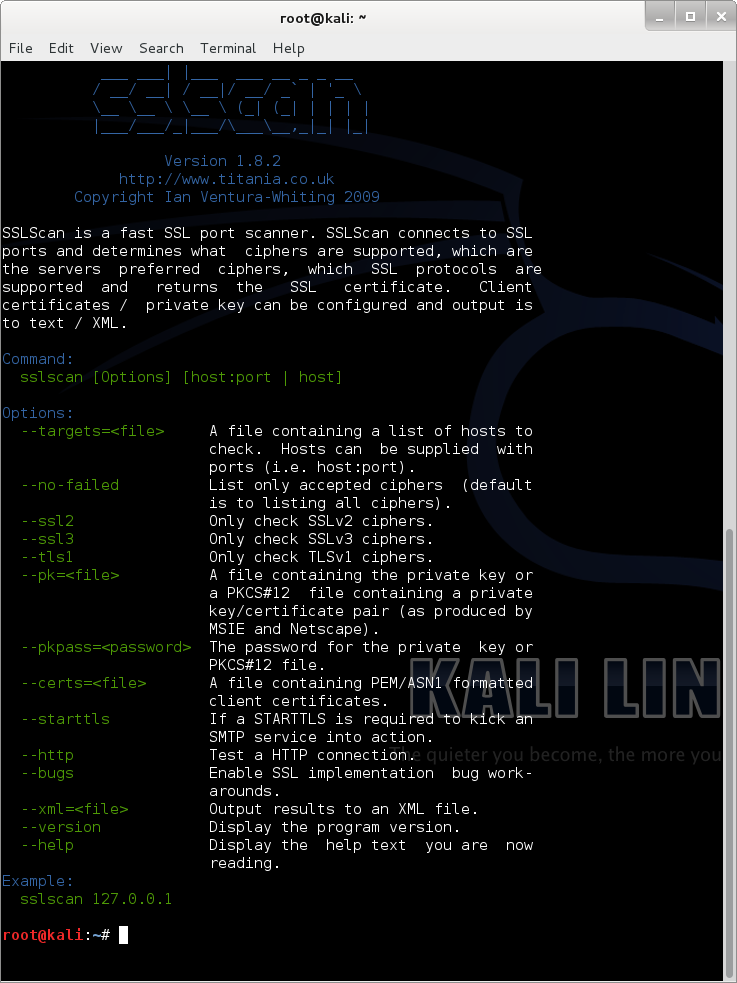
sslscan
SSLScan is a fast SSL port scanner. SSLScan connects to SSL ports and determines what ciphers are supported, which are the servers preferred ciphers, which SSL protocols are supported and returns the SSL certificate. Client certificates / private key can be configured and output is to text / XML.
sslyze
SSLyze is a Python tool that can analyze the SSL configuration of a server by connecting to it. It is designed to be fast and comprehensive, and should help organizations and testers identify misconfigurations affecting their SSL servers.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 | |
tlssled
ssl tls scanner
SMB Analysis
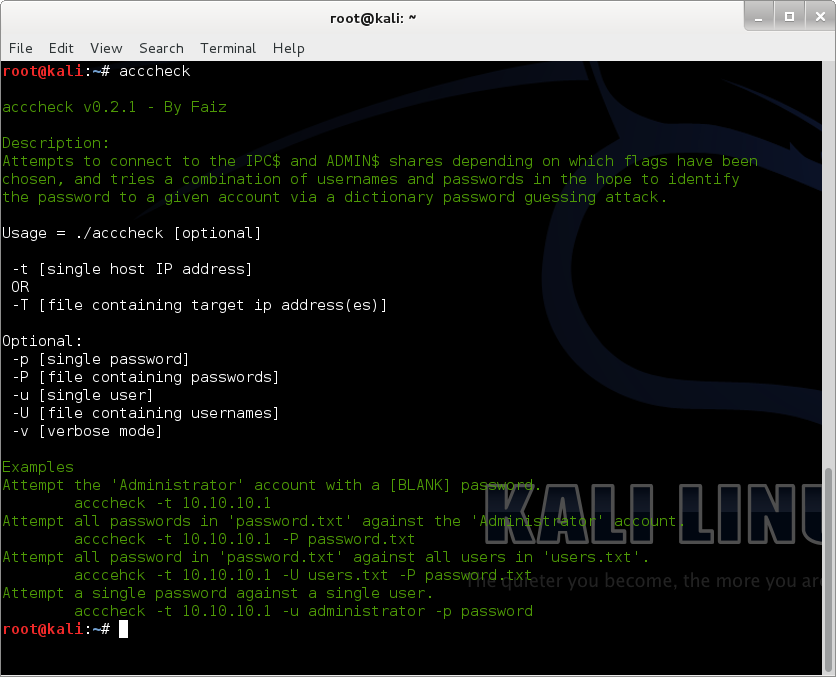
acccheck
Attempts to connect to the IPC$ and ADMIN$ shares depending on which flags have been chosen, and tries a combination of usernames and passwords in the hope to identify the password to a given account via a dictionary password guessing attack.
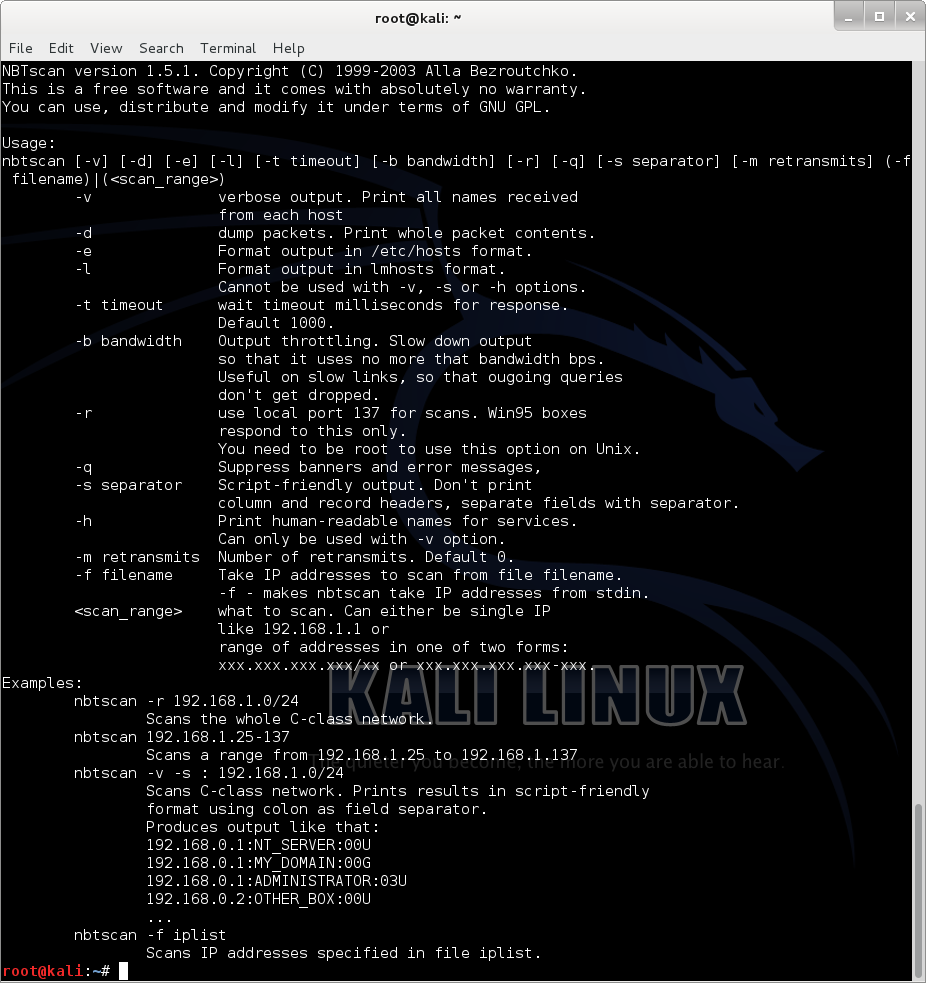
nbtscan
nbtscan is a program for scanning IP networks for NetBIOS name information. It sends NetBIOS status query to each address in supplied range and lists received information in human readable form. For each responded host it lists IP address, NetBIOS computer name, logged-in user name and MAC address (such as Ethernet).
SMTP Analysis
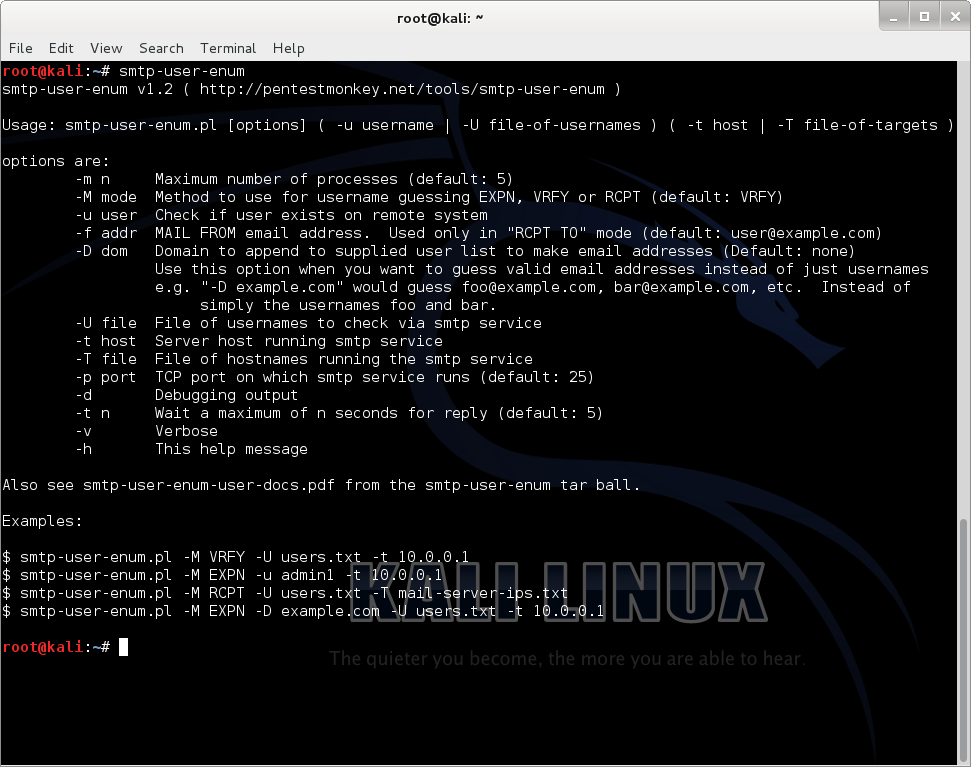
smtp-user-enum
Username guessing tool primarily for use against the default Solaris SMTP service. Can use either EXPN, VRFY or RCPT TO
swaks
Swiss Army Knife SMTP, the all-purpose smtp transaction tester
swaks’ primary design goal is to be a flexible, scriptable, transaction-oriented SMTP test tool. It handles SMTP features and extensions such as TLS, authentication, and pipelining; multiple version of the SMTP protocol including SMTP, ESMTP, and LMTP; and multiple transport methods including unix-domain sockets, internet- domain sockets, and pipes to spawned processes. Options can be specified in environment variables, configuration files, and the command line allowing maximum configurability and ease of use for operators and scripters.
SNMP Analysis
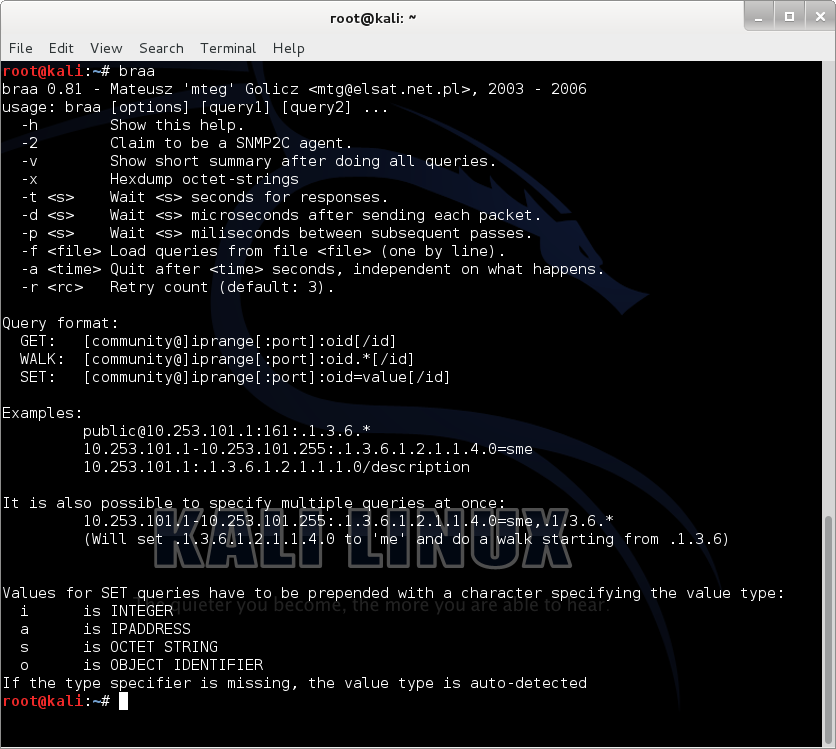
braa
Braa is a tool for making SNMP queries. It is able to query hundreds or thousands of hosts simultaneously, while being completely single-threaded. It does not need any SNMP libraries, as it is equipped with its own SNMP engine
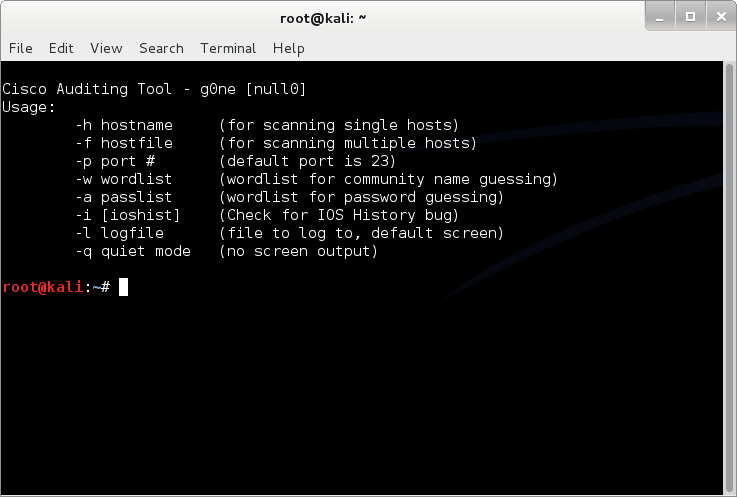
cisco-auditing-tool
Perl script which scans cisco routers for common vulnerabilities. Checks for default passwords, easily guessable community names, and the IOS history bug. Includes support for plugins and scanning multiple hosts.
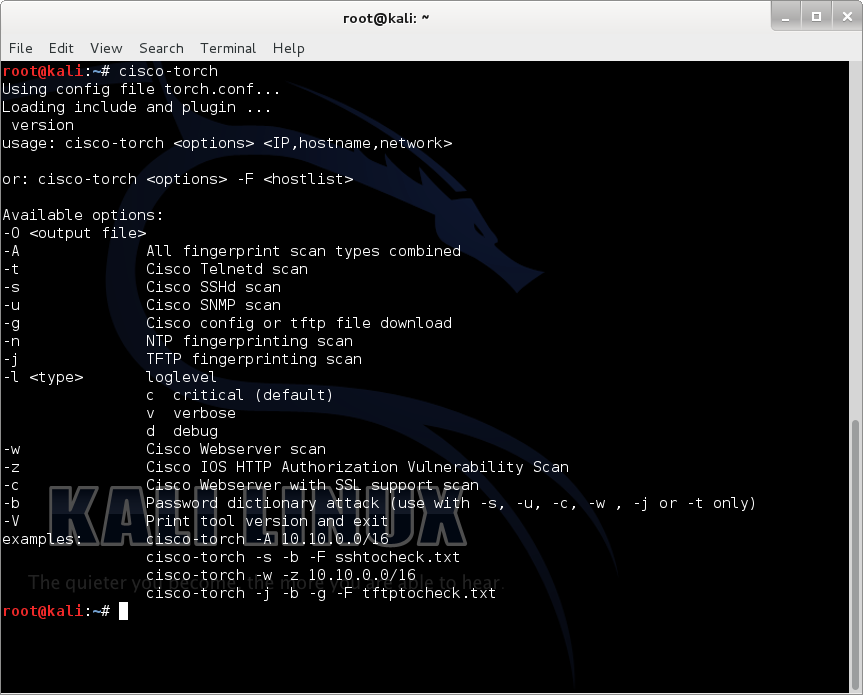
cisco-torch
mass scanning, application layer fingerprinting, and exploitation tool to discover and attack remote Cisco hosts running Telnet, SSH, Web, TFTP, NTP and SNMP services. Useful in auditing large networks for misconfigured/un-updated Ciscos.
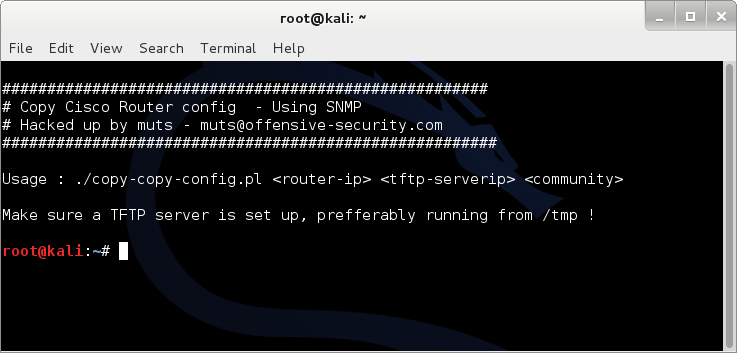
copy-router-config
copy an entire router configuration file from a Cisco device
merge-router-config
make changes to a Cisco router configuration file and merge those changes to a Cisco router
onesixtyone
simple SNMP scanner which sends requests for the sys‐Descr value asynchronously with user-adjustable sending times.
snmpcheck
SNMP device enumerator
SSL Analysis
sslcaudit
This tool is designed to automate testing SSL/TLS clients for resistance against MITM attacks
ssldump
ssldump is an SSL/TLS network protocol analyzer. It identifies TCP connections on the chosen network interface and attempts to interpret them as SSL/TLS traffic. When it identifies SSL/TLS traffic, it decodes the records and displays them in a textual form to stdout. If provided with the appropriate keying material, it will also decrypt the connections and display the application data traffic.
sslh
ssl/ssh multiplexer
sslsniff
sslsniff is designed to create man-in-the-middle (MITM) attacks for SSL/TLS connections, and dynamically generates certs for the domains that are being accessed on the fly. The new certificates are constructed in a certificate chain that is signed by any certificate that is provided. sslsniff also supports other attacks like null-prefix or OCSP attacks to achieve silent interceptions of connections when possible.
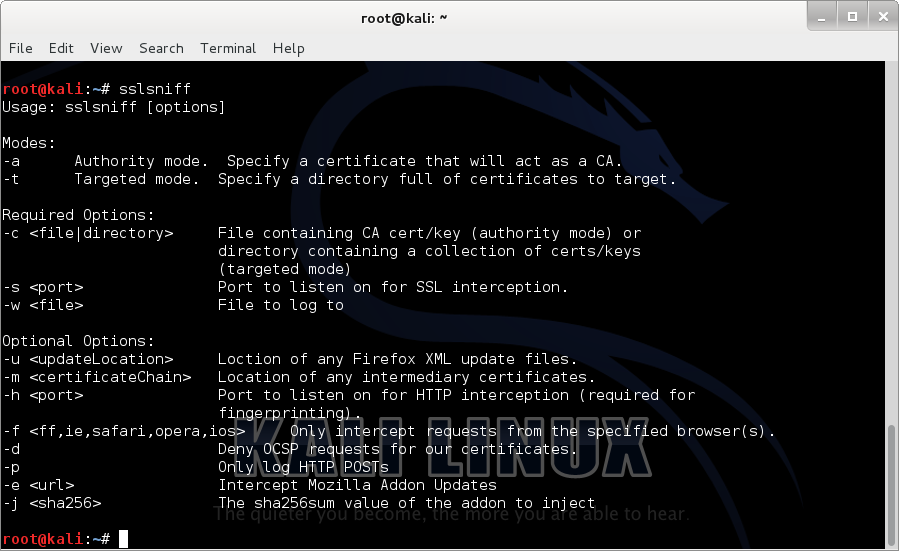
sslsplit
SSLsplit is a tool for man-in-the-middle attacks against SSL/TLS encrypted network connections. Connections are transparently intercepted through a network address translation engine and redirected to SSLsplit. SSLsplit terminates SSL/TLS and initiates a new SSL/TLS connection to the original destination address, while logging all data transmitted. SSLsplit is intended to be useful for network forensics and penetration testing.
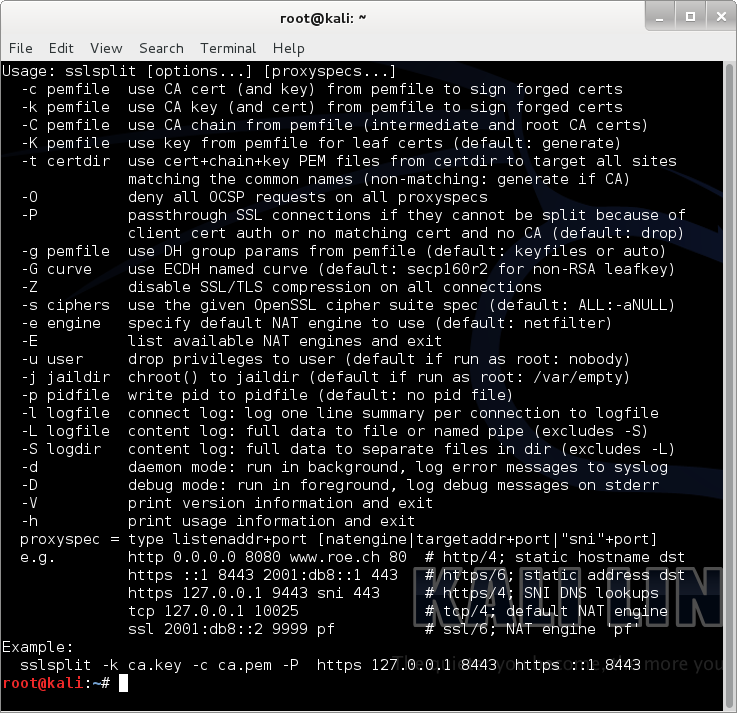
sslstrip
SSL/TLS man-in-the-middle attack tool
stunnel
The stunnel program is designed to work as SSL encryption wrapper between remote clients and local (inetd-startable) or remote servers. The concept is that having non-SSL aware daemons running on your system you can easily set them up to communicate with clients over secure SSL channels.
Telephony Analysis
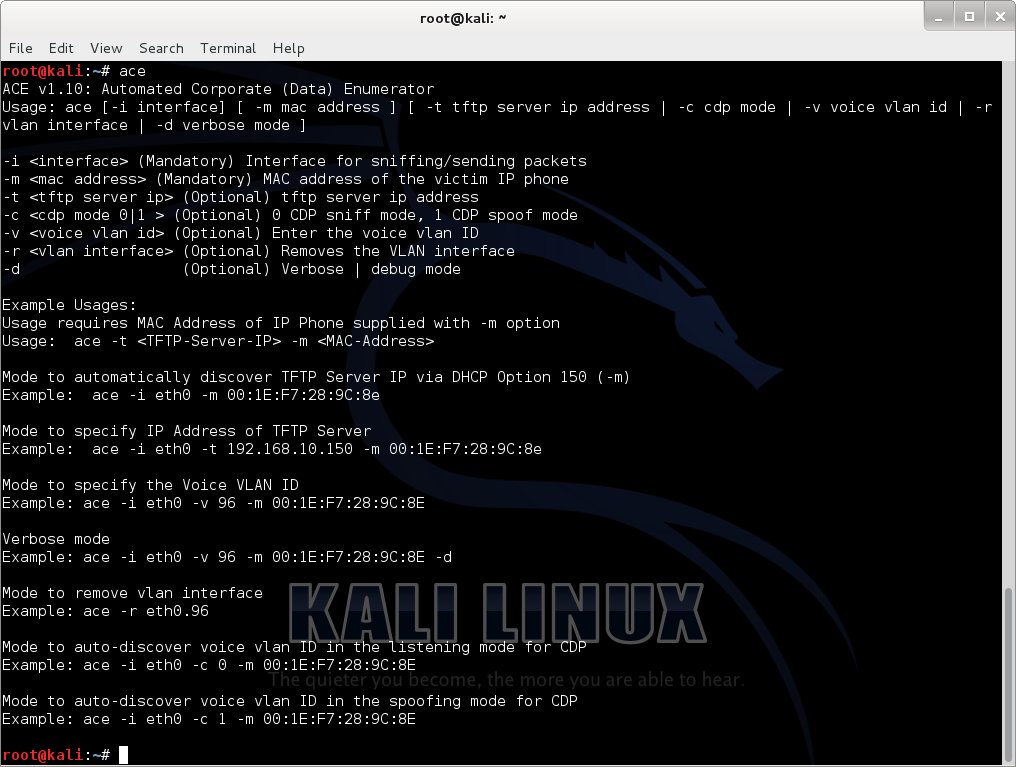
ace
Automated Corporate (Data) Enumerator
Traffic Analysis
irpas-ass
Autonomous System Scanner
irpass-cdp
This program is for sending CDP (Cisco router Discovery Protocol) messages to the wire.
p0f
P0f is a tool that utilizes an array of sophisticated, purely passive traffic fingerprinting mechanisms to identify the players behind any incidental TCP/IP communications (often as little as a single normal SYN) without interfering in any way.
Some of its capabilities include:
Highly scalable and extremely fast identification of the operating system and software on both endpoints of a vanilla TCP connection – especially in settings where NMap probes are blocked, too slow, unreliable, or would simply set off alarms,
Measurement of system uptime and network hookup, distance (including topology behind NAT or packet filters), and so on.
Automated detection of connection sharing / NAT, load balancing, and application-level proxying setups.
Detection of dishonest clients / servers that forge declarative statements such as X-Mailer or User-Agent.
tcpflow
tcpflow is a program that captures data transmitted as part of TCP connections (flows), and stores the data in a way that is convenient for protocol analysis or debugging.
wireshark
Wireshark is a GUI network protocol analyzer. It lets you interactively browse packet data from a live network or from a previously saved capture file.
VoIP Analysis
enumiax
enumIAX is an Inter Asterisk Exchange version 2 (IAX2) protocol username brute-force enumerator.
VPN Analysis
ike-scan
Discover and fingerprint IKE hosts (IPsec VPN servers)
1 2 3 4 5 6 7 8 9 10 | |
Ok, that took forever. I will make posts with the other categories as well.
The only way to keep your health is to eat what you don’t want, drink what you don’t like, and do what you’d rather not.
— Mark Twain