Today we’ll explore another tool for DNS enumeration: the DNS Network Mapper (dnsmap). Although at the time of this post, its last update was in 2010, this tool has survived the passage of time, and has been packaged with versions of both Backtrack and Kali. There is quite a wealth of information about the tool on its homepage, and it comes with a built-in wordlist for domain bruteforcing.
Homepage: https://github.com/makefu/dnsmap
dnsmap description
dnsmap was originally released back in 2006 and was inspired by the fictional story “The Thief No One Saw” by Paul Craig, which can be found in the book “Stealing the Network – How to 0wn the Box”
dnsmap is mainly meant to be used by pentesters during the information gathering/enumeration phase of infrastructure security assessments. During the enumeration stage, the security consultant would typically discover the target company’s IP netblocks, domain names, phone numbers, etc …
Subdomain brute-forcing is another technique that should be used in the enumeration stage, as it’s especially useful when other domain enumeration techniques such as zone transfers don’t work (I rarely see zone transfers being publicly allowed these days by the way).
LIMITATIONS
Lack of multi-threading. This speed issue will hopefully be resolved in future versions.
FUN THINGS THAT CAN HAPPEN
Finding interesting remote access servers (e.g.: https://extranet.targetdomain.com)
Finding badly configured and/or unpatched servers (e.g.: test.targetdomain.com)
Finding new domain names which will allow you to map non-obvious/hard-to-find netblocks of your target organization (registry lookups – aka whois is your friend)
Sometimes you find that some bruteforced subdomains resolve to internal IP addresses (RFC 1918). This is great as sometimes they are real up-to-date “A” records which means that it is possible to enumerate internal servers of a target organization from the Internet by only using standard DNS resolving (as oppossed to zone transfers for instance).
Discover embedded devices configured using Dynamic DNS services (e.g.: linksys-cam.com). This method is an alternative to finding devices via Google hacking techniques
USAGE
Bruteforcing can be done either with dnsmap’s built-in wordlist or a user-supplied wordlist. Results can be saved in CSV and human-readable format for further processing. dnsmap does NOT require root privileges to be run, and should NOT be run with such privileges for security reasons.
dnsmap options
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | |
dnsmap usage
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 | |
Here is how the output looks in the CSV format:
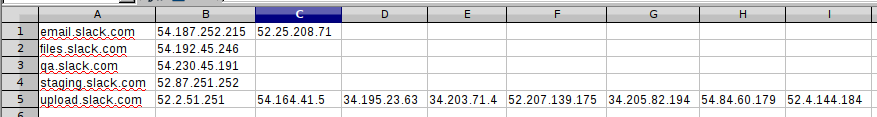
1 2 3 4 5 6 7 8 9 | |