It’s been a while since I’ve last polished my web hacking skills, and I recently found out about these CTF challenges. Too late for the bounty though..
You can access the labs at http://ctf.infosecinstitute.com/index.php
Level 1
This is straightforward, just listen to Yoda:

You can find the flag in the source: infosec_flagis_welcome
Level 2
Found the image in the source:
1
| |
When clicking on it, there is this error:
The image “view-source:http://ctf.infosecinstitute.com/img/leveltwo.jpeg%E2%80%9D cannot be displayed because it contains errors.
Downloaded it and ran strings on it:
1 2 | |
Well, well. This isn’t suspicious at all! :D After you Base64 decode it, you get the flag: infosec_flagis_wearejuststarting
Level 3

I used an online barcode scanner that produced this output: .. –. ..–. —– … . –.–. ..–. .–.. .– —. .. … — —– .–. … .. –. —.. Well, that seems familiar..Morse code! Used this site to decode it: INFOSECFLAGISMORSING
Level 4

If you hover over the image with your mouse, a popup appears with the message Stop poking me!. Looking in the source, the Javascript function responsible for that is called poke(), and you can find it in the custom.js file. All it does is alert the message. I spent some time here going in a wrong direction, disabling Javascript, and trying to see if something is hidden in the image. The hint states HTTP, and I did look at the headers and all, and it’s not often that you see a cookie called fusrodah. But initially I didn’t think it was pertaining to this specific level, because it was present in the requests to other levels as well. But when I hit a blank on everything else, I returned to it and ran it in some decoders:
1
| |
And I hit the jackpot with a Caesar shift of 13: infosec_flagis_welovecookies
Level 5
When you click on Level 5, you immediatelly get a popup saying Hacker!!!. I disabled Javascript to see this image:

Right, back to the thing I hate most, steganography. Stegdetect didn’t find anything, and I didn’t have any luck with StegExpose either. Surprisingly, an online tool came to help: https://futureboy.us/stegano/decinput.html
The output was this string:
1
| |
which I then ran in a binary decoder: infosec_flagis_stegaliens
Level 6
Packet analysis is not really my thing, so the way I solved this was by just following streams until I hit on something potentially interesting: the string 696e666f7365635f666c616769735f736e6966666564, contained in the first UDP packet, with a source and destination of 127.0.0.1. This was actually the hex encoded flag: infosec_flagis_sniffed
Level 7
I tried to manually navigate to levelseven.php and all I got was a blank page. But when I looked at the request with Live HTTP Headers, I noticed this: HTTP/1.0 200 aW5mb3NlY19mbGFnaXNfeW91Zm91bmRpdA==. A base64 encoded string…and decoding it gives the flag: infosec_flagis_youfoundit
Level 8
Well, didn’t expect to solve it just by running strings, but that’s all you need to do! :D The flag is in the strings output: infosec_flagis_0x1a
Level 9
No SQLi involved here..so I googled for Cisco IDS Web Login System password. Eventually I found the credentials that work on this page that contains default passwords for a number of devices. The ones that worked were root:attack. A popup appeared with the flag ssaptluafed_sigalf_cesofni, which is the reverse for infosec_flagis_defaultpass
Level 10
Played the .wav file, it sounded like something being fast forwarded. So I launched Audacity, and under Effect->Change Speed, you can play with the Speed Multiplier (some 0.20 and lower) until you hear a voice telling you the flag: infosec_flagis_sound
Level 11

Right, that huge PHP image is suspicious. I downloaded it and ran strings on it to begin with, and:
1
| |
Base64? Yes it is! Decoding it gives the address of another image: http://www.rollerski.co.uk/imagesb/powerslide_logo_large.gif

Couldn’t find anything hidden in this image, so I guess infosec_flagis_powerslide
Level 12

Spent some time scratching my head at this one, because I couldn’t find anything. Since I was just jumping over the initial section of the page source, with the CSS files and all, I was missing the relevant information. So, if you look in the source and you compare it with other pages, you can see that there is a new CSS file, called design.css, with the following inside:
1 2 3 | |
And if you decode that hex string, you get the flag: infosec_flagis_heyimnotacolor
Level 13
I kept trying editing the URL and adding file extensions commonly associated with backup files from this list. Eventually, stumbled upon one that works: the .old file extension.
Files that contain the .old file extension are most commonly used to indicate that a file on a user’s hard drive is a backup copy of a newer version of the file. The .old extension is given to the file name when the newer version of the file is saved within the associated computer application.
The initial file extension is often kept intact when the .old file extension is assigned to a file. For example, if the original version of a file is saved as mydocument.doc, then when a new version of the file is created that version will also be saved with the name of mydocument.doc. However, in order to store a copy of the old version of the file, the original version will be saved with the name as mydocument.doc.old.
So when I added .old to the URL, I got a message if I want to open or download levelthirteen.php.old. Ok, now we’re getting somewhere! Ran strings on it (again!) and noticed an extra something in the source:
1 2 3 4 5 6 7 8 9 | |
I went to http://ctf.infosecinstitute.com/misc/imadecoy and you can download the mysterious file. Apparently it’s another job for Wireshark:
1 2 | |
Ok, more random following streams and trying to glean what’s interesting. Eventually, I reached this part:
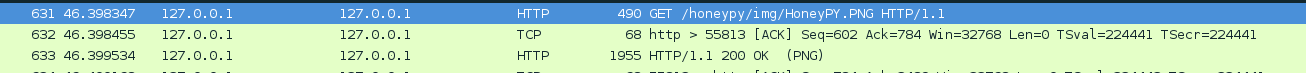
The GET request for that HoneyPY.PNG image occurs a few times after first spotting it. So the image might be interesting. And it’s possible to reconstruct it from the packet file! Click on the relevant packet:
1
| |
Then go to File->Export Objects->HTTP. Wireshark will then give you all the HTTP objects list:
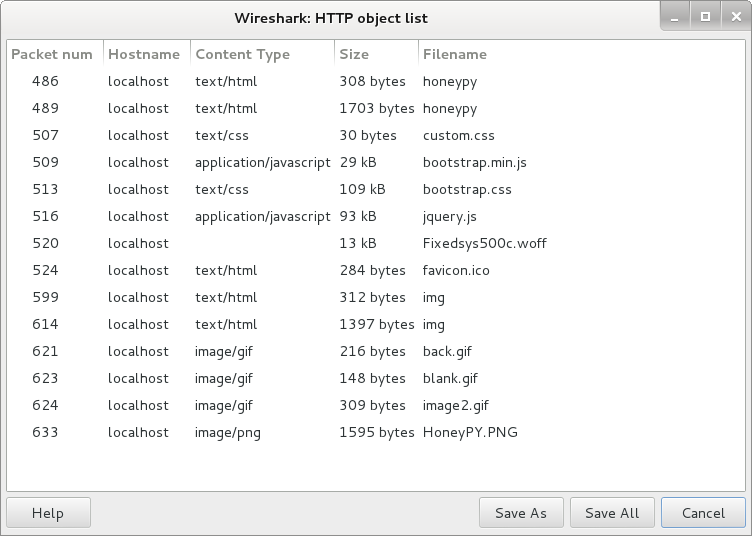
We’re only interested in the image, which is the last one. I saved it, and…
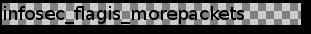
Level 14
The file is a phpMyAdmin SQL Dump. If you scroll through it, towards the end there will be this table:
1 2 3 4 5 6 7 8 | |
Used this decoder to decode the not-at-all conspicuous string and: infosec_flagis_whatsorceryisthis ! :D
Level 15
Something seems wrong with the server and I get a (real) 404 error for this level only. When it works again I will update this section