This is the final vulnerable machine in the Kioptrix series. To set it up in VMware, create a new virtual machine with the advanced options and use existing virtual disk, pointing it at the Kioptrix 4 virtual disk.
Let’s see what Nmap reveals:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 | |
Again, this seems to be a web based challenge. Navigating to the target website shows this:
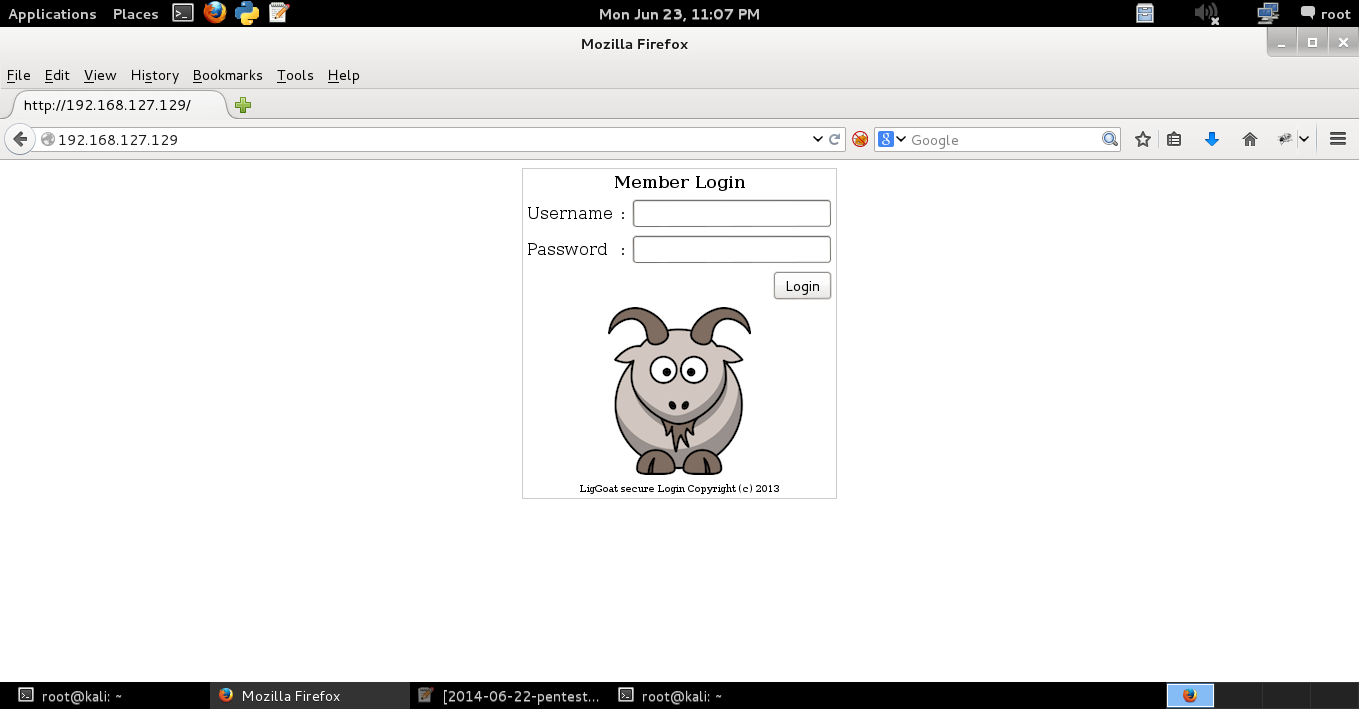
Supplying a single quote in the password field gives an error, which nicely discloses the database end as being MySQL:
Warning: mysql_num_rows(): supplied argument is not a valid MySQL result resource in /var/www/checklogin.php on line 28 Wrong Username or Password
Sqlmap to the rescue!
1 2 3 4 5 6 7 8 9 10 11 | |
Logging in with these credentials didn’t yield anything though, all I could see was a member’s control panel with no functionality. So I remembered the previous challenge that allowed SSH access, and tried to log in:
1 2 3 4 5 6 7 8 9 10 11 | |
Excellent! It’s time for some sniffing around. This is not a normal shell, usual commands don’t work, so let’s see what’s available with the help system.
1 2 | |
Hmm, not much. Actions are restricted too, can’t cd to wherever I want:
1 2 3 4 | |
So I googled for a bit, and it appears this shell is a Python based limited shell (https://github.com/ghantoos/lshell):
lshell is a shell coded in Python, that lets you restrict a user’s environment to limited sets of commands, choose to enable/ disable any command over SSH (e.g. SCP, SFTP, rsync, etc.), log user’s commands, implement timing restriction, and more.
It is possible to escape from this shell by leveraging the echo command to call os.system in order to spawn a shell: echo os.system(‘/bin/bash’)
1 2 3 | |
Poking around, I found the following information in /var/www/john/john.php:
1 2 3 | |
So, root doesn’t have a password for MySQL? Let’s check:
1 2 3 4 5 6 | |
Here I have found a way to get root privileges from a MySQL server running as root. Here’s a quick summary:
It is possible to escalate from MySQL server root level to system root by using User Defined Functions (UDF)
We need the lib_mysqludf_sys.so library that contains some useful functions that can interact with the OS. The most important ones are sys_exec (executes the command and returns the exit status) and sys_eval (executes the command and returns the standard output)
The next step would be to find a way to get the library on the machine with our MySQL server. But that’s not necessary in this case, because it’s already on the server!
1 2 | |
It took a bit of googling and trial and error until I found a way that worked in getting me to a root shell. Here is a useful post. The relevant part for us is this:
Until Ubuntu 11.10, the Unix group for administrators with root privileges through sudo had been admin. Starting with Ubuntu 12.04 LTS, it is now sudo, for compatibility with Debian and sudo itself. However, for backwards compatibility, admin group members are still recognized as administrators
So it is possible to make the john account to be part of the admin group, that is equivalent to the sudo group. So from the MySQL prompt, run this:
1
| |
What that does is it modifies john’s account, appending it to the admin group. So let’s do it on the MySQL command line:
1 2 3 4 5 6 7 | |
Now from john’s shell:
1 2 3 4 | |
Awesome! We finally got root access! In root’s directory there is another congrats.txt file that tells us there are at least 2 different tested ways to get root on this system. It sure was an interesting machine, and my favorite in the series, because it wasn’t as straightforward as the others, and I had to look for more information and try (and fail) different approaches before I hit upon the winning one.
Here’s today’s fortune cookie:
You single-handedly fought your way into this hopeless mess.